
by Chris | Feb 1, 2026 | Blog
1. Introduction: The Fragile State of SMB Data The Status Quo of SMB Storage For Small-to-Medium SaaS providers (SMEs), storage is frequently the most vulnerable link in the architectural chain. In the early stages of a project, the natural tendency is to rely on...

by Chris | Jan 21, 2026 | Blog
1. The Modern SaaS Dilemma: The Gap Between Scale and Skill In the current landscape, mid-sized SaaS providers face a systemic paradox. To remain competitive, they adopt modern, distributed architectures—containers, microservices, and hybrid clouds. However, the human...

by Chris | Jan 11, 2026 | Blog
The “Running is Enough” Fallacy In early-stage startups, the mantra is often “speed over everything.” Infrastructure is typically a reflection of this lean structure: a single monolithic server, manual backups, and a prayer against hardware...

by Chris | Jan 9, 2026 | Blog
I. Introduction The landscape of software engineering has undergone a tectonic shift over the last decade. Historically, an application might have resided on a single monolithic server with a predictable relational database. Today, we operate in an era of...
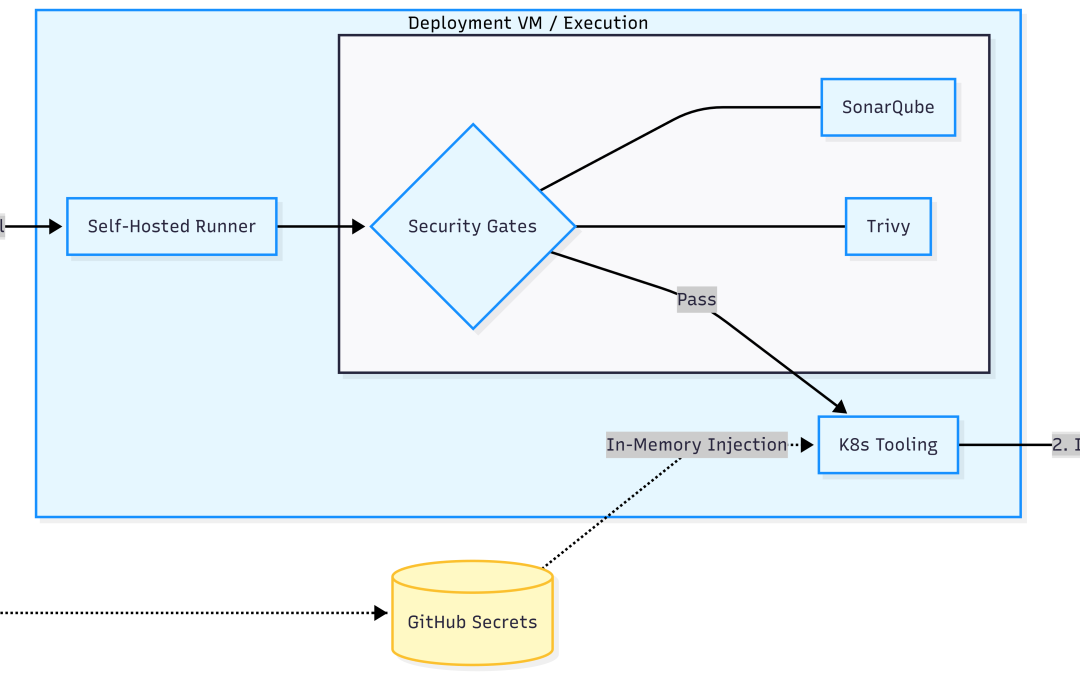
by Chris | Jan 7, 2026 | Blog
In Part 1, we established the “Frontline” of our SaaS—a hardened perimeter consisting of DMZ isolation and Layer 7 WAF scrubbing. However, a secure boundary is only half the battle. In a Modern SaaS environment, the greatest risk often lies in how we build...
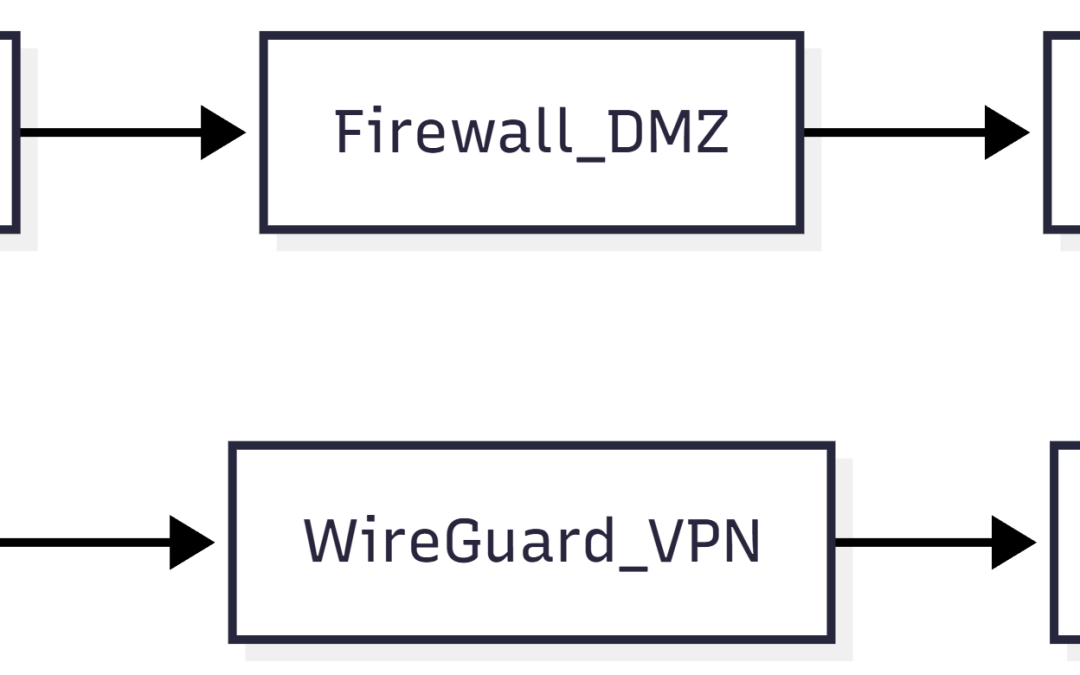
by Chris | Jan 4, 2026 | Blog
Introduction: The Trinity of the SaaS Frontline For a modern SaaS provider, the “Frontline” is not a single device. It is a strategic security complex that separates core data assets from the chaos of the internet and from the risks inside the corporate office. Many...







