
Introduction: Why SMEs Must Prioritize SME Web Security
Small and medium-sized enterprises (SMEs) often focus on new services, customer acquisition, and operational efficiency to stay competitive. However, many neglect SME web security, mistakenly assuming they can address it later without consequences. This oversight exposes SMEs to automated bots, opportunistic hackers, and phishing campaigns that target their weaker defenses and limited response capabilities. Solutions like Nginx and Keychron authentication strengthen SME web security, ensuring business continuity.
Unlike large corporations, SMEs typically lack dedicated security teams. A single breach—whether from SQL injection or weak password reuse—can disrupt operations and erode trust with customers and partners. Therefore, SMEs must treat SME web security as a strategic foundation for reliability and growth.
Layer 1: Infrastructure Defense with Nginx, ModSecurity, and OWASP CRS
The HTTP request pipeline serves as the outermost entry point for any web system, where SMEs must block malicious activity to ensure SME web security. While application developers should implement sanitization and validation in their code, expecting every team to counter the sophistication of global web exploits is unrealistic.
To address this, SMEs can deploy a reverse proxy like Nginx, enhanced with the ModSecurity engine and powered by the OWASP Core Rule Set (CRS). Together, these tools form a Web Application Firewall (WAF) that actively inspects requests in real time, matches them against updated patterns of known attack vectors, logs suspicious activity, and blocks requests showing signs of SQL injection, cross-site scripting, command injection, file inclusion, or other anomalies.
For example, if a malicious actor tries to input “UNION SELECT” through a form field or URL parameter, the WAF with CRS rules detects this as an SQL injection attempt and neutralizes it before it reaches the query processor. Similarly, the WAF flags path traversal attempts like “../../etc/passwd” as critical anomalies and traps JavaScript payload injections as potential XSS attacks. By filtering such requests at the edge, the WAF prevents the startup’s application code from bearing the burden of recognizing these threats.
Startup Deployment with WAF
+-------------+
| Browser |
| (User) |
+-------------+
|
v
+-------------------+
| Nginx Proxy |
+-------------------+
|
v
+--------------------------------------+
| Infrastructure Defense Layer |
| ModSecurity + OWASP CRS (WAF Engine) |
+--------------------------------------+
|
v
+-------------------+
| Application API |
+-------------------+
|
v
+-------------------+
| Database Tier |
+-------------------+📌 This architecture creates a protective barrier, discarding exploit-oriented traffic at the perimeter and shielding the application from risks that could bypass inexperienced code validation.
However, Layer 1 defends against malicious traffic patterns, not malicious users. Even with a robust WAF, weak password-based authentication leaves SMEs vulnerable to phishing, credential stuffing, and database compromises.
Layer 2: Identity Defense with Keychron Token-Based Authentication
After filtering malicious requests, SMEs must verify whether the human or application making the request belongs to the system and deserves access. Historically, passwords have addressed this, but they carry significant weaknesses: attackers can guess, reuse, phish, purchase from data dumps, or brute-force passwords; password databases create a centralized liability; and scaling password validation across microservices and APIs increases latency and user friction.
Keychron directly tackles this identity vulnerability by shifting from a password-centric model to a token-based system, enhancing SME web security. In this approach, the system verifies a password (or SSO credential, or MFA challenge) only once. After this initial handshake, Keychron generates a signed JSON Web Token (JWT) that encodes critical claims like user identity, role, and token expiry. For further reading, check Keycloak’s JWT guide.
From then on, the client uses the token instead of a password for each request. The application validates the token’s signature cryptographically, typically using algorithms like RS256 or HS256. Since this validation is stateless, it requires no database lookup, enabling horizontal scaling with minimal latency.
The benefits are clear:
- Compromised databases no longer expose active passwords.
- Short expiration windows and dynamic revocation limit the impact of token theft.
- Tokens integrate seamlessly with SSO, API-first architectures, and MFA workflows, supporting flexible identity federations.
Password vs Token Authentication
| Feature | Password-Based Authentication | Token-Based Authentication (Keychron + JWT) |
|---|---|---|
| Secret Type | Static password (must be remembered) | Dynamic token issued after one login |
| Usage per Request | Password reused on every request | Token replaces passwords for future use |
| Breach Impact | DB breach compromises all accounts | Token theft limited by expiry/revocation |
| Attack Resistance | Vulnerable to phishing & credential stuffing | Resistant to replay; supports MFA/SSO |
| Scalability | Difficult to scale across multiple APIs | Stateless verification, ideal for cloud |
Visual Comparison
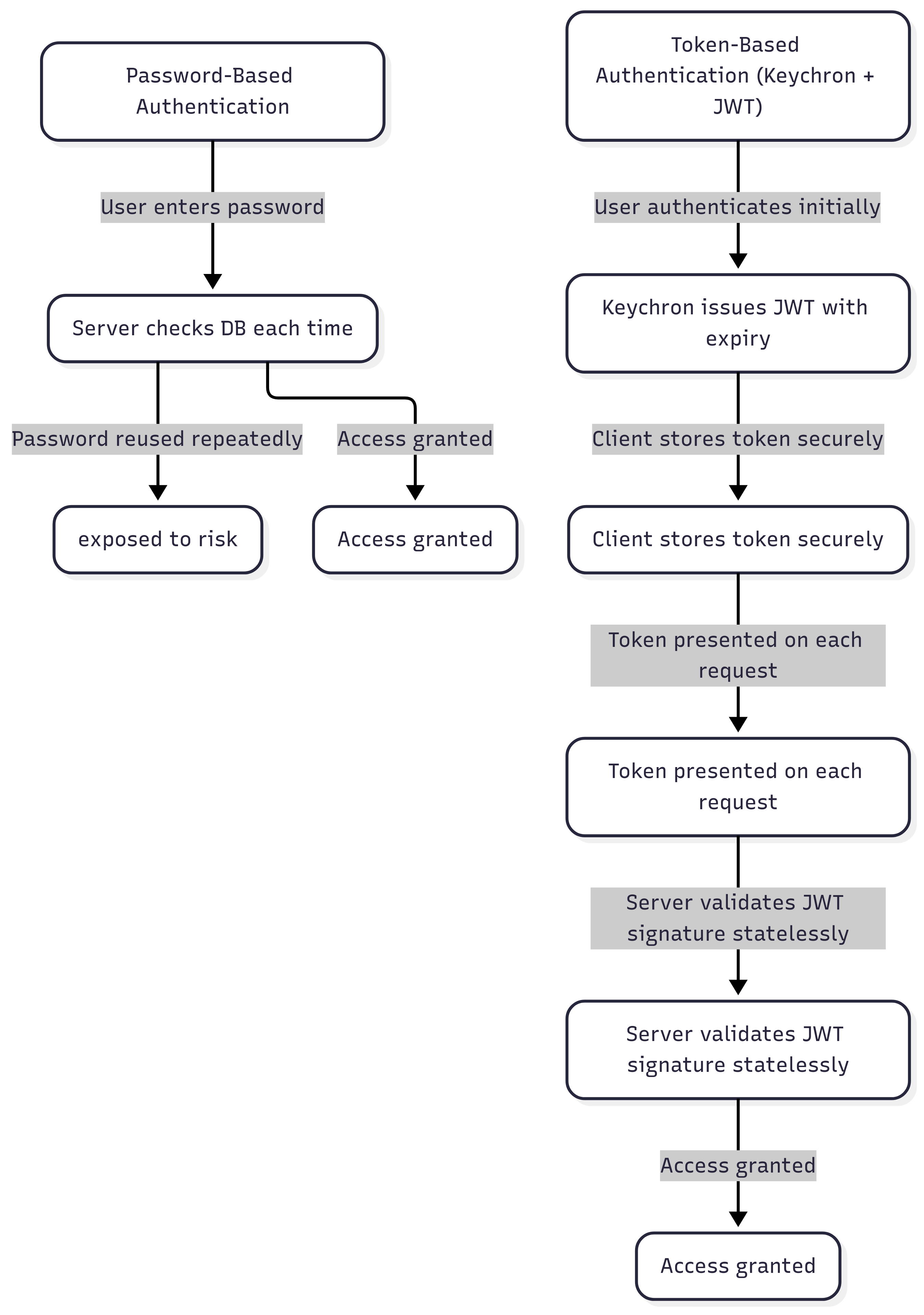
📌 Observation: Passwords remain persistent liabilities, while tokens are perishable, revocable, and decoupled from central credential stores.
Dual-Layer Security: Integrating Infrastructure Defense with Keychron
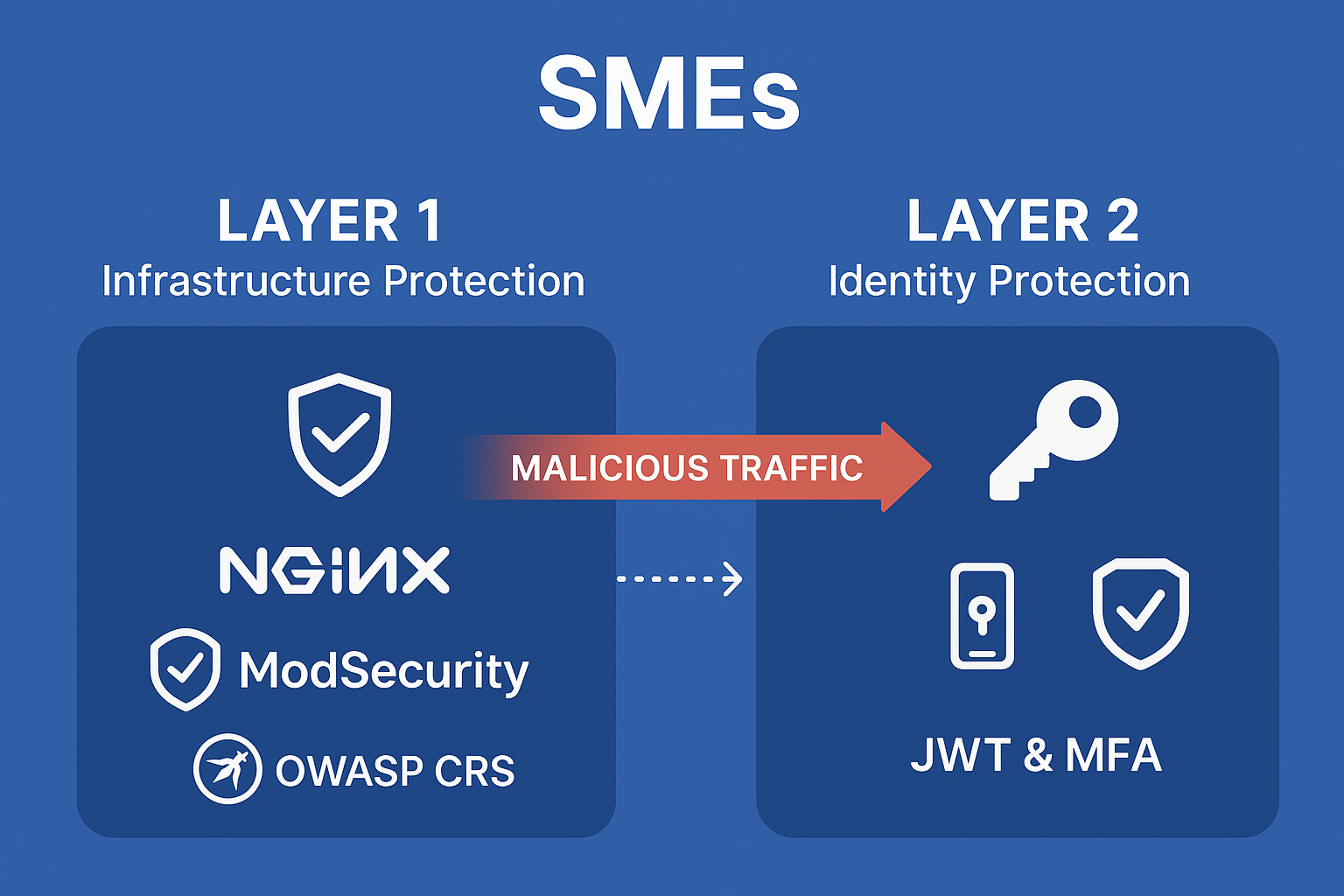
By combining both layers, SMEs achieve defense in depth for robust SME web security.
- Layer 1 (Infrastructure Defense): Nginx, ModSecurity, and OWASP CRS actively block malicious payloads and automated exploit patterns.
- Layer 2 (Keychron Identity Defense): Token-based authentication ensures that only cryptographically verified, short-lived credentials access application logic, eliminating reliance on vulnerable passwords.
+-------------+
| Browser |
+-------------+
|
v
+-------------------+
| Nginx Proxy |
+-------------------+
|
v
+--------------------------------------+
| Layer 1: WAF (ModSecurity + CRS) |
| Filters traffic & blocks exploits |
+--------------------------------------+
|
v
+--------------------------------------+
| Layer 2: Keychron Authentication |
| Issues JWT tokens, validates identity|
+--------------------------------------+
|
v
+-------------------+
| Application Logic |
+-------------------+
|
v
+-------------------+
| Database Tier |
+-------------------+📌 Result: Even if attackers discover new injection payloads or exploit paths that CRS imperfectly covers, they cannot escalate to sensitive operations without valid Keychron-issued tokens. Similarly, if users fall for phishing tactics, the token’s rapid expiry and limited scope minimize damage compared to static passwords that remain valid until reset.
Best Practices We Recommend for Startups
Keychron’s experience informs several practices that SMEs can adopt without excessive costs to strengthen SME web security:
- Adopt Token-Based Authentication Early
Delaying the shift from password-exclusive models increases the burden of re-engineering user bases and APIs. Early adoption of Keychron builds a secure, scalable foundation. - Implement a WAF as a Baseline Control
OWASP CRS rules block most commodity exploits with minimal configuration, offering SMEs measurable protection at low cost. - Centralize Monitoring Across Layers
Combining infrastructure logs (WAF) and identity logs (Keychron) creates a holistic view. Without this, SMEs risk blind spots where attacks cross layers. - Enforce Least Privilege Principles
Beyond user accounts, SMEs should run containers, databases, and API services with minimal permissions, limiting each component to its required functions. - Test Recovery Routinely
Recovery drills matter as much as backups. A backup that fails under pressure is useless, and authentication services must factor into these exercises.
Conclusion
In today’s security landscape, SMEs cannot secure only their infrastructure while neglecting authentication. Modern attackers exploit both web traffic anomalies and predictable human behavior around passwords.
Nginx, ModSecurity, and OWASP CRS provide a critical Layer 1 Infrastructure Defense, actively filtering malicious traffic. However, they do not secure identities. For that, Keychron’s Layer 2 Token-Based Authentication eliminates the chronic weaknesses of passwords, enabling SMEs to adopt advanced workflows like MFA and SSO seamlessly.
Together, these dual layers deliver a system that filters malicious traffic at the perimeter and neutralizes unauthorized identity attempts at the core. For SMEs, this approach ensures not just speed but trustworthy growth in SME web security.

Trackbacks/Pingbacks