SME software architecture balances Predictability, Security, and Cloud-Native Practices
Introduction
Small and medium-sized enterprises (SMEs) face increasing pressure to adopt cloud-first strategies, as cloud platforms promise scalability, speed, and flexibility. However, these advantages often come with hidden and unpredictable costs—including data transfer charges, storage growth, and fluctuating compute workloads. For SMEs with limited IT budgets, such variability can lead to financial strain. Moreover, compliance risks, vendor lock-in, and over-dependence on third-party infrastructure reduce control over sensitive data and long-term sustainability.
An on-premises software architecture that selectively integrates cloud-native practices provides a balanced solution: maintaining control of critical systems, ensuring predictable IT costs, while benefiting from modern scalability and automation.
Detail
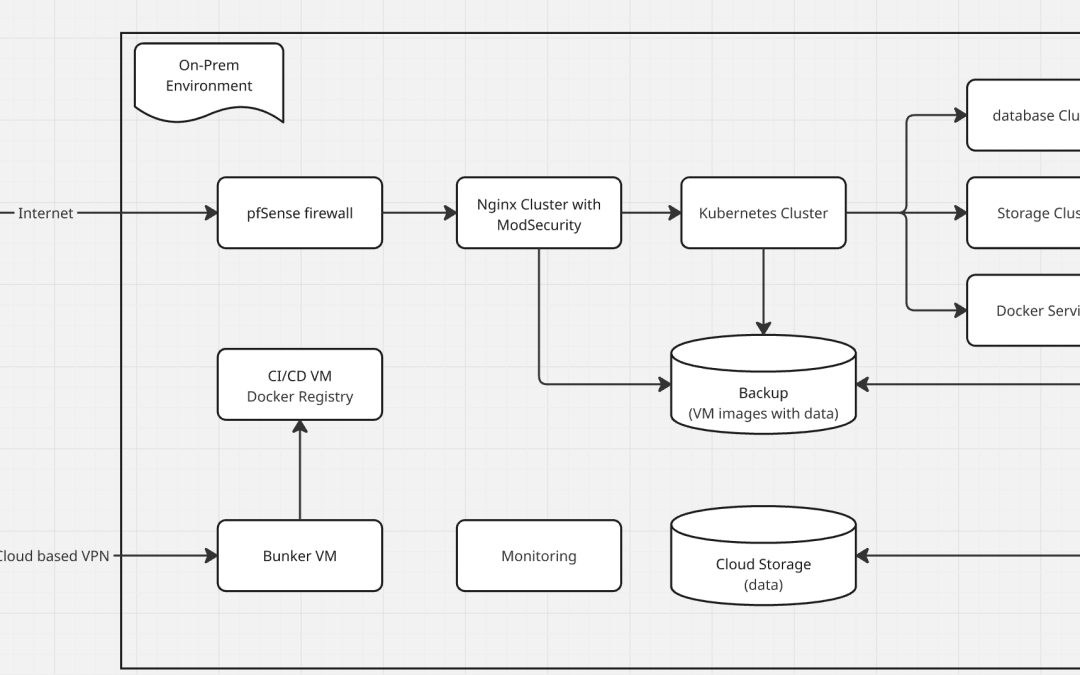
1. Security & Access Control for SMEs
For SMEs, safeguarding sensitive data and systems is paramount to maintaining customer trust and regulatory compliance. This architecture employs a multi-layered security model that segments access for external users and internal staff, reducing the risk of unauthorized access or data breaches. By combining advanced firewall protections, secure VPNs, and zero-trust principles, it ensures robust defense against common cyber threats. The setup is designed to be both cost-effective and manageable, making it ideal for small businesses with limited IT resources.
- Users (Clients/Customers):
- Access only through HTTPS.
- Entry point secured by pfSense firewall, filtering unwanted traffic.
- Requests are routed through Nginx with ModSecurity (OWASP CRS), acting as both reverse proxy and Web Application Firewall (WAF).
- This setup mitigates common web attacks such as SQL injection, XSS, and OWASP Top 10 threats, while also balancing traffic loads across backend services.
- Reference: Protecting SMEs with Nginx + ModSecurity.
- Staff (Internal Operators & Developers):
- Staff do not access internal systems directly over the public internet.
- Instead, they connect through cloud-based VPNs such as ZeroTier or Tailscale, which provide encrypted overlay networking.
- Once authenticated, staff access the Bunker host, a controlled jump point to internal resources.
- Internal traffic is secured with self-signed certificates and mutual TLS, ensuring that even within the private network, trust is explicitly verified.
- This model creates a zero-trust environment, where every connection is authenticated and encrypted, minimizing lateral movement risk.
- Reference: Secure Remote Access Guide.
This layered security strategy—combining perimeter firewall, WAF, VPN isolation, and zero-trust verification—ensures robust protection for SMEs.
2. Application & Data Layer for Scalability
The application and data layer is engineered to provide SMEs with the flexibility to scale operations while maintaining reliable performance for critical systems. By separating stateless and stateful workloads, this architecture optimizes resource utilization and simplifies management for small IT teams. Containerized applications enable rapid scaling, while dedicated virtual machines ensure stability for data-intensive services. Comprehensive backup strategies further enhance resilience, protecting against data loss and ensuring business continuity.
- Containerized Applications:
- Deployed on a Kubernetes cluster for flexible, scalable stateless workloads.
- Kubernetes orchestration enables rolling updates, failover, and service discovery.
- Stateful Services:
- Critical components like databases, Redis, and shared storage run on dedicated VMs, not Kubernetes.
- This separation ensures consistent performance, simplified data synchronization, and reduced complexity in managing stateful sets.
- Data integrity is maintained with daily VM snapshot backups stored locally, plus cloud object storage (Wasabi) for offsite redundancy.
- This dual-backup approach mitigates hardware failure and site-level disaster risks.
This hybrid approach enables dynamic scaling for stateless services and stable, recoverable stateful services.
3. CI/CD & Software Supply Chain Security
Implementing CI/CD pipelines is essential for SMEs to stay competitive, but public exposure of development tools can introduce significant security risks. This architecture prioritizes secure, internal automation to protect the software supply chain while enabling efficient development workflows. By hosting CI/CD runners within the private network, it minimizes external dependencies and vulnerabilities. This approach ensures that SMEs can adopt modern DevOps practices without compromising on security or incurring unpredictable costs.
- Public Exposure Approach (High Risk):
- Hosting a Docker registry or Kubernetes dashboard publicly would allow cloud-native automation but expose sensitive services to the internet.
- Even with authentication, such exposure increases the attack surface, making it vulnerable to credential theft, misconfiguration, or zero-day exploits.
- It also introduces dependency on external certificate management and monitoring, further complicating operations.
- Internal Self-Hosted Runner Approach (Adopted):
- GitHub Actions self-hosted runners are deployed within the secure internal network.
- CI/CD pipelines interact directly with Kubernetes and the internal Docker registry, secured by internal CA-signed certificates.
- No sensitive API endpoints or registries are exposed publicly, ensuring secure DevOps automation.
This self-hosted model delivers modern CI/CD benefits without compromising security or increasing external dependencies.
Conclusion
This on-premises software architecture is tailored for SMEs navigating modern IT challenges. By integrating firewall and WAF protection, VPN-based staff isolation, Kubernetes scalability, VM-based stateful services, dual-backup systems, and secure CI/CD pipelines, it offers:
- Predictable IT costs without cloud billing volatility.
- Robust security through layered defense and zero-trust access.
- Operational control and compliance by managing critical services internally.
- Scalability and modernization via selective cloud-native practices.
This balanced IT foundation empowers SMEs to grow sustainably, avoiding unpredictable cloud costs while maintaining a secure, scalable, and future-ready architecture.