I. Introduction: The Silent Threat to the Modern Pipeline
Modern cyberattacks rarely begin at the application’s external interface. Attackers now target the software supply chain—the dependencies, components, and build artifacts that development teams trust by default. For small and medium-sized enterprises (SMEs) with 10 to 100 engineers, fast delivery cycles often create a Security–Velocity Paradox. Teams move quickly, but they reduce scrutiny of third-party dependencies and build processes.
This risk is structural. OWASP A03:2025 – Software Supply Chain Failures, Scenario #4, identifies a critical design assumption in modern systems: components usually run with the same privileges as the application itself. When a team introduces a vulnerable or malicious dependency, that component immediately gains full application-level authority. A single flaw can therefore compromise the entire system.
SMEs face higher exposure because of how they operate. Teams work in decentralized environments. Developers select dependencies implicitly. Transitive dependencies often remain unexamined. Each unverified library or container layer expands the application’s trusted computing base without improving visibility or accountability. Risk accumulates inside the CI/CD pipeline long before deployment. OWASP also highlights environments where patching is difficult or impossible, such as IoT and embedded systems. In these cases, a compromised component creates long-lived exposure. Downstream controls offer little remediation once the system grants trust.
The conclusion is unavoidable. Software supply chain security is now a primary attack surface. SMEs must stop treating the build pipeline as inherently trustworthy. Instead, they must treat it as a potential adversarial surface that requires continuous verification.
II. Defense-in-Depth Architecture for Software Supply Chain Security
SMEs cannot mitigate OWASP A03:2025 with isolated tools or reactive controls. They need a defense-in-depth DevSecOps architecture embedded into the delivery pipeline. This architecture enforces trust incrementally and validates it automatically at each stage of the lifecycle.
The model defines three sequential trust boundaries: source code, build artifacts, and final binaries. Each boundary enforces a specific security objective. Each produces a clear pass-or-fail decision before promotion. This structure directly addresses the OWASP A03:2025 failure mode where vulnerable components inherit full runtime privileges. The goal is prevention, not detection after deployment.
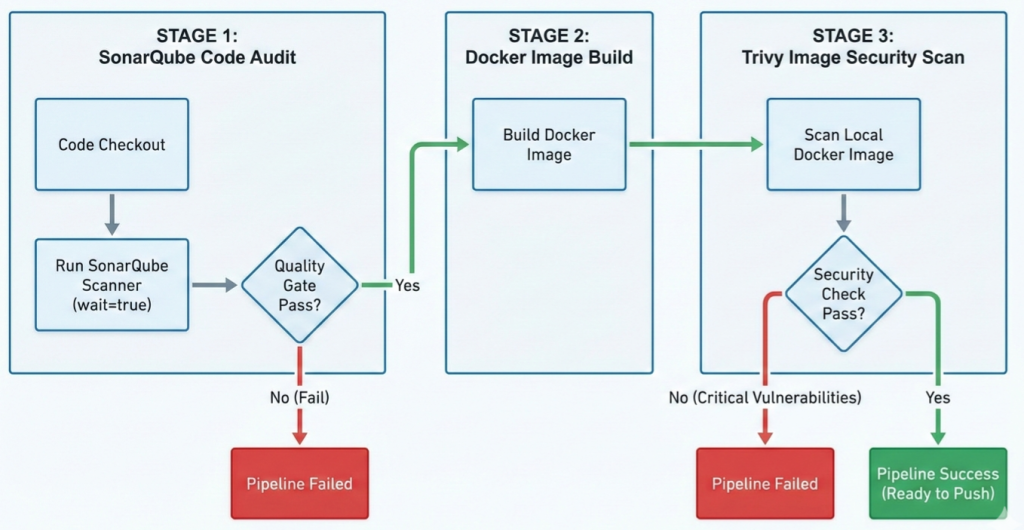
1. Persistent Source Code Governance (SonarQube)
The first trust boundary is the source code. This framework treats source governance as continuous infrastructure, not an optional review step. Manual code review cannot scale for teams approaching 100 engineers. It also fails to detect security patterns consistently.
Every commit triggers automated static analysis with a focus on security posture. SonarQube evaluates Security Hotspots, including unsafe cryptography, improper input handling, and overly permissive APIs. These weaknesses often enable privilege escalation when a compromised dependency exists.
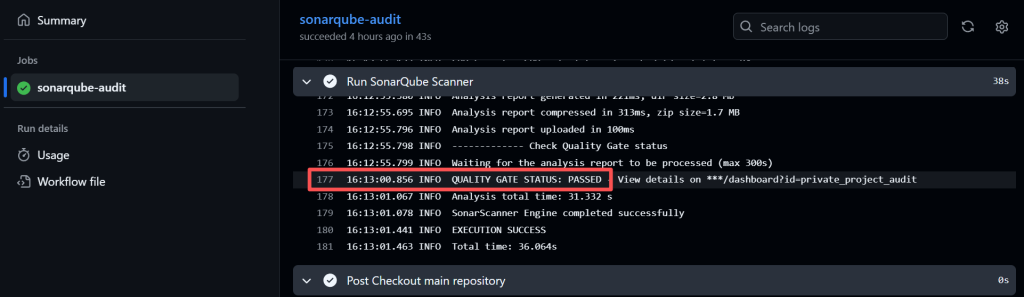
Quality Gates enforce compliance. If code fails the defined security thresholds, the pipeline stops. This rule is absolute. First-party code must not amplify third-party risk. SonarQube ensures internally written logic does not become the weakest link in the supply chain.

2. Artifact Sanitization and Secret Decoupling in Containerized Builds
The second trust boundary is the build artifact. Containerization improves portability, but it also preserves everything included during the build. Supply chain failures often occur when teams embed secrets directly into container layers.
This architecture enforces a strict rule: container images must remain identity-neutral. Images must not contain secrets or persistent configuration files. The pipeline generates configuration dynamically using CI/CD-managed variables. Runtime injection or transient memory holds sensitive data.
This separation converts containers into sanitized execution units. Even if attackers compromise an image registry, they gain only executable logic. They do not gain credentials that enable broader infrastructure compromise. Artifact sanitization limits blast radius by design.
3. Binary Integrity Validation and Vulnerability Threshold Enforcement (Trivy)
The final trust boundary evaluates the compiled artifacts. At this stage, the focus shifts from code quality to component composition and embedded dependencies. Each binary bundle has transitive components that may carry security risks.
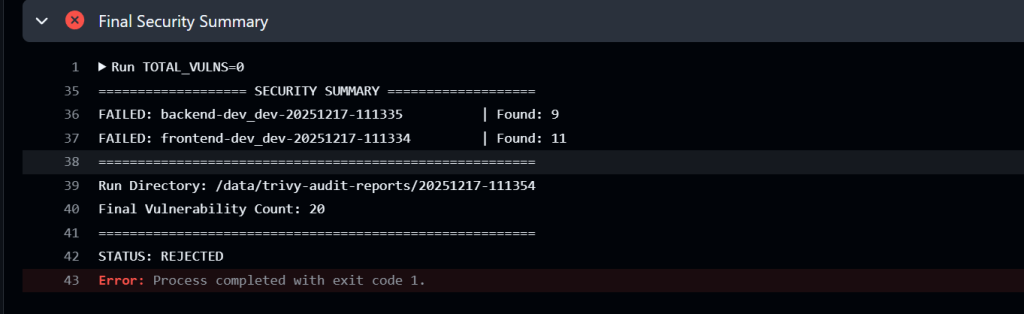
In our GitHub CI/CD Pipeline example as screenshot above, Trivy scans both frontend and backend container images for known vulnerabilities in the pipeline. The system enforces quantified risk thresholds: any artifact containing High severity vulnerabilities is automatically rejected. In regulated environments, the threshold may be tightened to Medium.
This enforcement acts as a hard stop. When Trivy detects vulnerabilities in an image, the pipeline fails immediately, preventing the compromised artifact from progressing to deployment. This ensures that only secure, verified components reach production.
III. Conclusion: Integrating the Chain of Integrity
Mitigating OWASP A03:2025 – Software Supply Chain Failures requires treating the delivery pipeline as a security boundary. It cannot remain a passive deployment mechanism. For SMEs with 10 to 100 engineers, this defense-in-depth DevSecOps architecture creates enforceable trust boundaries where compromise spreads fastest.
By governing source code, container artifacts, and binary composition in sequence, the pipeline becomes an active security control. Automated decisions occur early and consistently. Vulnerable or over-privileged components never reach production.
This approach moves SMEs away from reactive incident response. It enables architectural resilience, where design constrains supply chain risk before failure occurs.
Further Reading
OWASP A01: WAF, ModSecurity, and RBAC Layered Defense
https://www.chriscn.cn/owasp-a01-waf-modsecurity-and-rbac-layered-defense/Hybrid Cloud for SMBs: Tackling Security Misconfigurations
https://www.chriscn.cn/hybrid-cloud-smbs-security-misconfiguration/DevOps Release Strategy: Why SIT, UAT, and Progressive Delivery Still Matter
https://www.chriscn.cn/devops-release-strategy-why-sit-uat-and-progressive-delivery-still-matter/