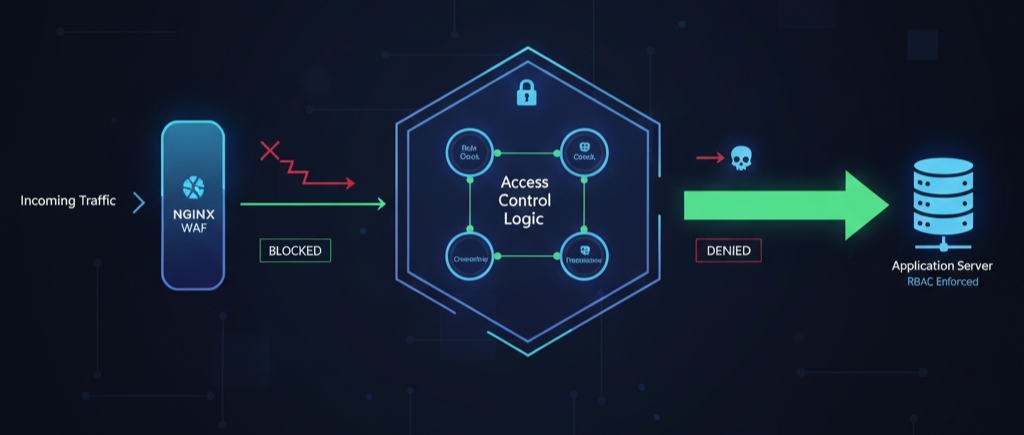
Introduction: Why A01 Remains the Top Security Risk
Broken Access Control (OWASP A01) consistently ranks as the most prevalent and critical security vulnerability (refer to the official OWASP Top 10:2025 A01 Guide). This flaw occurs when users can perform actions outside of their intended permissions, leading to unauthorized data disclosure or privilege escalation. To effectively tackle this, a layered approach is mandatory, combining external security measures like WAF and ModSecurity with core application logic such as RBAC (Role-Based Access Control) for authoritative decisions and robust IDOR Prevention.
The challenge lies in the sheer complexity of modern applications, where fragmented authorization logic often leads to security gaps. OWASP emphasizes that access control must be implemented in trusted server-side code where the attacker cannot tamper with the checks.
To build a truly robust defense, a single-layer approach is insufficient. We advocate for a Defense-in-Depth model that integrates Nginx/ModSecurity (WAF) for perimeter enforcement with Server-Side Role-Based Access Control (RBAC) for authoritative authorization.
Common Access Control Vulnerabilities and the Two-Layer Defense
OWASP outlines several common access control failures. Our layered solution maps directly onto these threats, assigning responsibility to the most efficient component:
| OWASP A01 Vulnerability (Threat) | Primary Defense Layer | Prevention Strategy |
|---|---|---|
| Violation of Least Privilege (Deny by Default) | Server-Side RBAC | RBAC enforces explicit permissions; implicitly denies all unlisted actions. |
| Insecure Direct Object References (IDOR) | Server-Side RBAC | Mandatory Ownership Check within application logic (using User ID and Resource ID). |
| Bypassing checks (Parameter Tampering/Force Browsing) | Nginx/ModSecurity (WAF) | Blocks unauthenticated access to secure routes and filters common probing patterns. |
| Exposed API routes for POST/PUT/DELETE | RBAC/WAF | RBAC enforces method permissions; WAF enforces authentication presence. |
| CORS Misconfiguration | Nginx/ModSecurity (WAF) | Nginx enforces strict Origin Header policies at the edge. |
| Elevation of Privilege | Server-Side RBAC | RBAC verifies the authenticated user’s assigned role and capabilities. |
Layer 1: Nginx and ModSecurity for Perimeter Hardening
The WAF layer, typically implemented using Nginx and the ModSecurity engine running the OWASP Core Rule Set (CRS), acts as a high-performance traffic cop. Its primary goal is to shed clearly unauthorized or malicious requests before they impact application performance or exploit potential logic gaps. You can find the engine source on ModSecurity’s GitHub Repository.
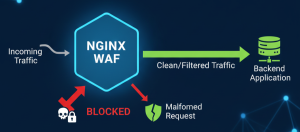
1. Enforcing Authentication and Path Restrictions
WAF can immediately reject requests that are structurally unsound or attempt to access restricted paths without meeting minimum requirements. This aligns with the OWASP principle of minimizing access and disabling directory listings.
Example: Blocking Unauthenticated Requests to Secure APIs
The WAF ensures that a request must at least present an authentication token before reaching the application logic:
# ModSecurity Rule Example: Deny if Authorization header is missing on secure path
SecRule REQUEST_URI "@beginsWith /api/secure" "id:10001,phase:2,t:none,deny,status:401,
msg:'Missing Auth Header for secure access', chain"
SecRule &REQUEST_HEADERS:Authorization "@eq 0"2. Force Browsing and Metadata Protection
WAF, particularly when leveraging the OWASP Core Rule Set (CRS), is excellent at blocking low-hanging fruit:
- URL Guessing: Blocking requests to non-existent or internal paths (
/admin_backup/,.git/). - Rate Limiting: Implementing rate limits on API and controller access to minimize harm from automated attack tooling (a key OWASP recommendation).
- Input Normalization: Sanitizing requests to defeat encoding and obfuscation attempts.
Layer 2: Authoritative Server-Side RBAC
The RBAC system is the trusted source of truth for all authorization decisions. It must be implemented to enforce record ownership and the principle of least privilege.
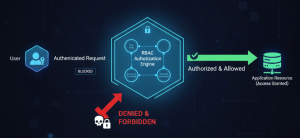
1. Implementing Deny by Default and Centralization
Access control must be implemented once and reused throughout the application (e.g., via middleware or decorators), rather than being scattered in individual controllers.
- Logic: Every action is denied unless the user’s role grants an explicit permission (e.g.,
user:read,post:delete). - Metadata Tampering: The server-side code relies solely on the decrypted, server-verified session or JWT data, preventing client-side manipulation (such as abusing JWT invalidation or hidden fields to elevate privileges).
2. Preventing Insecure Direct Object References (IDOR)
IDOR (Insecure Direct Object Reference) is the process by which an attacker modifies a parameter pointing to an object (e.g., an ID in a URL or request body) to directly access, modify, or delete a resource they do not own. IDOR (e.g., Scenario #1) is the most common form of A01, and its remediation requires enforcing contextual authorization—the user must not only have the permission to edit a post, but the right to edit that specific post.
The most effective prevention technique involves modifying the data access layer:
- Database Enforcement: When performing a CUD (Create, Update, Delete) operation, the database query must explicitly filter by the authenticated user’s ID.
IDOR Prevention Logic (Pseudocode for an Update):
UPDATE records SET data=? WHERE record_id = [client_id] AND owner_user_id = [server_authenticated_user_id];If the
owner_user_iddoes not match, the query fails silently, and the application returns a 403 Forbidden, preventing the IDOR.
3. Logging and Auditing
The RBAC component is the ideal place to log access control failures (as recommended by OWASP), providing crucial audit trails and triggering alerts for repeated failures, indicating an active attack.
Conclusion: Synthesis and Robustness
| Defense Principle | WAF (Nginx/ModSecurity) | RBAC (Application Core) |
|---|---|---|
| OWASP Core Principle | Minimize Access/CORS Control | Trusted Server-Side Check/Deny by Default |
| IDOR Mitigation | Mitigates automated scanning attempts (Rate Limit) | Enforces Record Ownership via Query |
| Vulnerability Focus | Protocol Abuse, Force Browsing, Malformed Requests | Privilege Escalation, Data Tampering, Logic Bypass |
| Testing Role | Checks for basic authentication presence (Unit/Integration Test) | Checks all functional access controls (Unit/Integration Test) |
The combined approach ensures that the application is protected at the edge from overwhelming or malicious traffic, while the core RBAC ensures that every access decision—especially those involving sensitive data and ownership—is precise, consistent, and fully controlled by the trusted server environment. This architecture provides the necessary resilience to stand firm against the evolving threat landscape of Broken Access Control.
Enforcement must be layered, consistent, and always occur on the trusted server side.
Further Reading on Architecture
For those interested in how this security framework fits into a larger, cost-effective, and scalable architecture designed for small and medium enterprises (SMEs), please visit my previous article: