Introduction: The Trinity of the SaaS Frontline
For a modern SaaS provider, the “Frontline” is not a single device. It is a strategic security complex that separates core data assets from the chaos of the internet and from the risks inside the corporate office. Many mid-sized providers fail because they treat the data center as an extension of the office network.
A rational Frontline Architecture integrates three tightly coupled pillars:
- The DMZ Enclave: A dual-layer firewall structure that physically decouples the SaaS production environment from the corporate office network.
- Layer 7 Scrubbing (WAF): An Nginx-based inspection layer that sanitizes public traffic before it reaches application logic.
- The Secure Access Path (VPN + Bunker): A stealthy, 2FA-hardened entry point for administrative access.
Only when these three pillars work together does the system form a true Security Enclave. In such an enclave, a compromised marketing laptop cannot become a pivot point for a database breach.
The DMZ: Strategic Isolation at the ISP Edge
A professional SaaS frontline starts with structural isolation. The production environment must not share the same security boundary as the enterprise network. As shown in the DMZ Architecture Diagram, the data center sits inside a dedicated security zone at the ISP entry point.
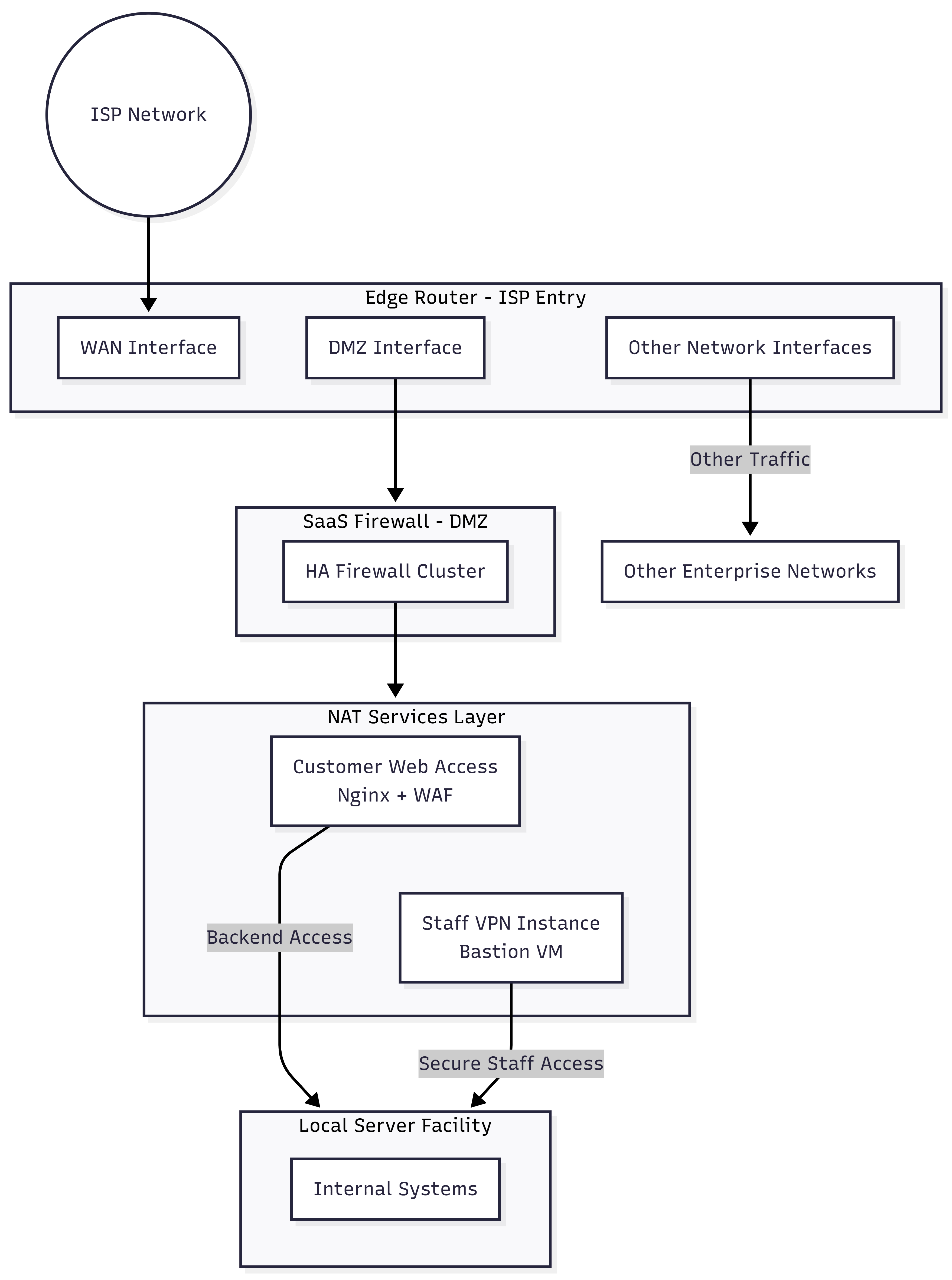
This boundary, defined at the Edge Router, turns the SaaS environment into an independent enclave. It physically and logically separates the Corporate Office Network from the SaaS Production Network. This separation eliminates the risk of lateral movement. Even if an office workstation is compromised, the frontline acts as a permanent firebreak that blocks any pivot into the data center.
From an operational perspective, this design gives SRE teams full independence. They can deploy aggressive firewall rules, replace edge hardware, or reconfigure NAT policies without disrupting office VoIP, printers, or staff Wi-Fi. By terminating the frontline directly at the ISP using local hardware, the organization converts network security into a predictable fixed-asset investment. This approach avoids the variable “cloud tax” and per-gigabyte inspection fees common in cloud-native gateways, while fully utilizing high-speed links.
In summary, the DMZ is not optional. It enforces physical and logical separation, strengthens resilience against internal and external threats, and creates an operationally agile and cost-efficient foundation for the SaaS platform.
Layer 7 Scrubbing: The Public User Path (Nginx + WAF)
Firewalls control network access, but they cannot interpret malicious intent hidden inside encrypted HTTPS traffic. As illustrated in the Nginx + WAF Flowchart, the Public User Path requires a dedicated Layer 7 inspection layer.
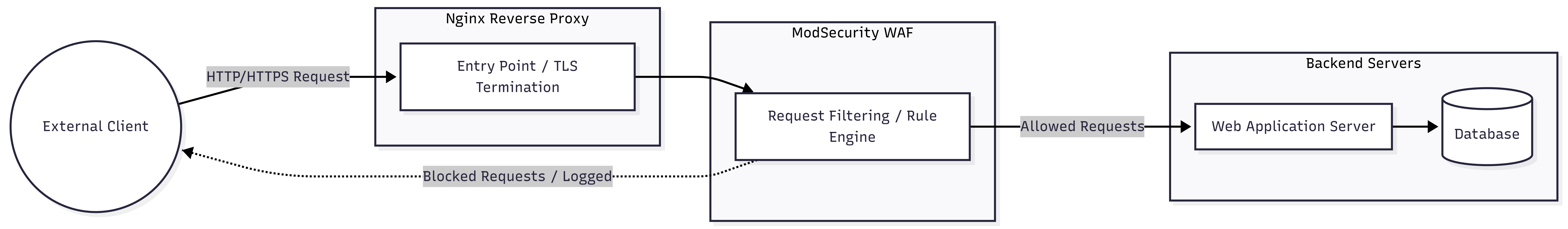
An Nginx cluster combined with a ModSecurity WAF performs deep request inspection at the edge of the DMZ. This layer actively mitigates OWASP A01: Broken Access Control by detecting and blocking SQL injection, Cross-Site Scripting (XSS), and malformed payloads before they reach application logic.
From an operational standpoint, this architecture enforces clean separation of concerns. The WAF handles TLS termination and traffic sanitization, which removes this burden from backend microservices. Developers can focus on business logic instead of duplicating security filters across APIs. This centralization also simplifies auditing and policy tuning.
From a cost perspective, the open-source stack scales horizontally without vendor lock-in. Teams can increase scrubbing capacity by adding local compute nodes instead of paying per-request or per-rule fees imposed by proprietary cloud WAFs.
In summary, Layer 7 scrubbing converts the public entry point into an intelligent security filter. By concentrating security intelligence at the Nginx layer, the backend remains a protected black box that balances high throughput with strong application security.
Administrative Integrity: The Secure Staff Path (WireGuard + 2FA Bunker)
Administrative access represents the highest-risk entry point in the data center. It grants full control over infrastructure and must resist both external compromise and insider abuse. As shown in the VPN + Bunker Sequence Diagram, the Secure Staff Path replaces IP whitelisting with an identity-driven access model.
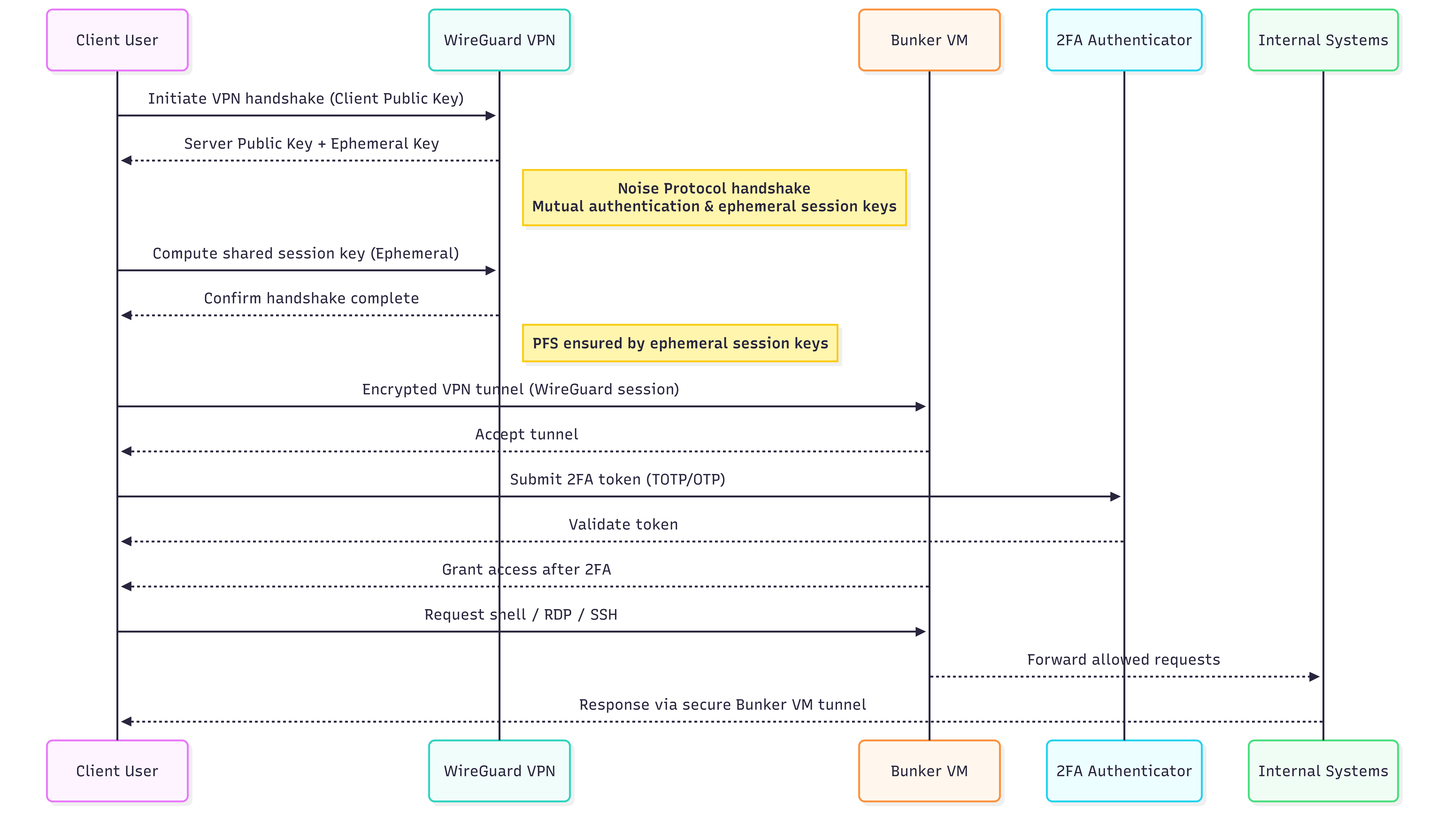
The architecture uses WireGuard as the VPN tunnel. WireGuard remains cryptographically silent to unauthorized probes, which makes management services invisible to internet scans. After the tunnel forms, a triple-lock control model takes effect. Engineers can only access a restricted Bunker VM (Jump Box). They must also pass a mandatory TOTP-based 2FA challenge before issuing any commands to internal systems.
This design creates a single auditable choke point. Security teams can record, monitor, and review every administrative session from one location. This capability directly supports SOC2 and GDPR compliance requirements.
From a cost standpoint, the self-hosted model removes recurring per-user license fees common in enterprise VPN products. The organization retains full ownership of encryption keys, access policies, and audit logs, regardless of team size.
In summary, the WireGuard and Bunker VM model delivers a zero-trust administrative path that is stealthy, auditable, and efficient. It ensures that privileged access only occurs through a hardened, 2FA-validated gateway while preserving low-latency performance for engineers.
Summary: Building a Rational Frontline Architecture
A hardened SaaS frontline depends on three integrated pillars: DMZ isolation, Layer 7 WAF scrubbing, and a 2FA-protected management bunker. Together, they create a resilient buffer between the public internet and the production core.
The dual-layer firewall model fully decouples the corporate office from the service network. This separation removes lateral movement risk and preserves the data center as a secure, isolated island. By relying on open-source tooling and local hardware, the architecture delivers strong security and operational autonomy while keeping costs predictable.
This frontline is not just defensive infrastructure. It is the hardened foundation upon which a scalable, compliant, and resilient SaaS platform is built.