In the rapidly evolving landscape of Cloud-Native development, the intersection of Multi-Tenant SaaS and Large Language Model (LLM) integration has introduced unprecedented complexity to access control. As organizations shift from monolithic structures to distributed microservices, the traditional method of embedding authorization logic within application code has become a significant liability. Therefore, this article explores why decoupling policy from logic via the PEP (Policy Enforcement Point) + PDP (Policy Decision Point) pattern is the only viable path for securing modern SaaS platforms and complex AI RAG workflows.
1. The Convergence of SaaS, Microservices, and AI: A Security Deadlock
The modern software industry is currently defined by the transition toward sophisticated Multi-Tenant SaaS platforms. These platforms orchestrate complex, multi-model LLM workflows where data is no longer static. Instead, data is processed through Retrieval-Augmented Generation (RAG) pipelines involving embeddings, vector databases, and multiple inference models. Consequently, providing a seamless yet secure experience where diverse organizations share a single infrastructure has become the gold standard for operational efficiency.
However, as these systems scale, developers face a “Logic Explosion.” In a microservices architecture, if each service manages its own authorization manually, the system becomes a fragmented mess of hardcoded “if-else” statements. Maintaining consistency across dozens of services eventually becomes impossible. For instance, a single change in a global policy requires a full redeployment of the entire ecosystem. Moreover, this fragmentation creates security “shadow areas” where inconsistent policy implementation allows for catastrophic cross-tenant data leakage.
The solution lies in architectural decoupling. We must move authorization out of the service logic and into a centralized, externalized authority. By implementing a PEP+PDP framework, organizations can finally treat Policy as Code. This approach centralizes decision-making while distributing enforcement. As a result, every service, database call, and LLM invocation is governed by a single, verifiable source of truth.
2. The Power of Unified Decision-Making: Why PEP + PDP is Essential
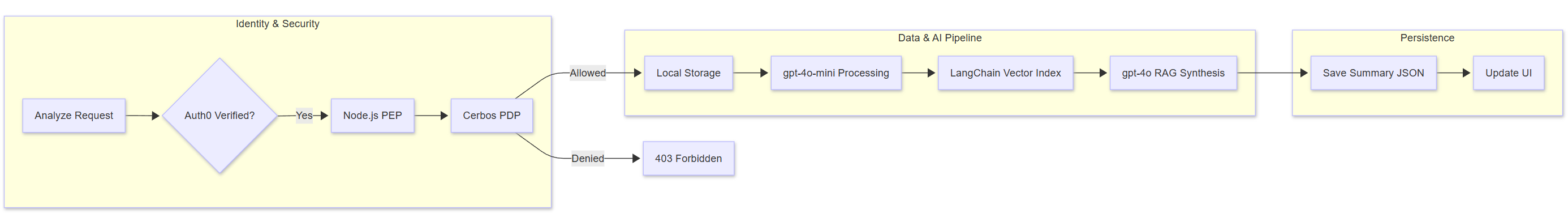
The core of this architecture is the functional separation of Enforcement (PEP) from Decision (PDP). The Policy Enforcement Point (PEP) lives within your application to intercept requests and ask, “Is this allowed?” Meanwhile, the Policy Decision Point (PDP), such as Cerbos, receives the full context of the request. It evaluates the request against pre-defined policies and returns a simple “Allow” or “Deny.”
The Multi-Tenant Isolation Imperative
In a SaaS environment, “Soft Isolation” is prone to human error and SQL injection vulnerabilities. By moving this logic to the PDP, we implement Hard Logical Isolation. Using Attribute-Based Access Control (ABAC), we define a global rule: A principal can only access a resource if their tenant IDs match. Because the PDP evaluates this rule, the microservice does not need to know how to filter data. It simply follows the decision, which drastically reduces the surface area for data breaches.
Protecting the LLM Workflow and AI Resources
AI models are the most expensive and sensitive resources in a modern stack. A multi-model RAG workflow involves multiple stages, such as embedding, retrieval, and synthesis. Without a PDP, controlling who can trigger which model becomes an operational nightmare. However, with a centralized PDP, we can gate the analyze action based on dynamic conditions. These include tenant subscription tiers, time-of-day, or even usage quotas. Consequently, this ensures that a “Free Tier” tenant cannot trigger a high-cost GPT-4o analysis reserved for “Enterprise” users.
Consistency Across Cloud-Native Microservices
Cloud-native systems thrive on heterogeneity. Services might be written in Node.js, Go, or Python. A centralized PDP provides a language-agnostic API that ensures the exact same policy applies to every service. Whether a user accesses a file via the Web UI or a background API, the decision remains consistent. Ultimately, this eliminates the “Policy Drift” that occurs when different teams implement authorization differently across the same system.
3. Case Study: Implementing the JSON RAG Manager
GitHub link: https://github.com/ChrisXHLeung/jsonRAG
The provided JSON RAG Manager project serves as a concrete implementation of these principles. It demonstrates how to secure a multi-tenant file manager with integrated AI summary capabilities.
Principal Identity and Tenant Extraction
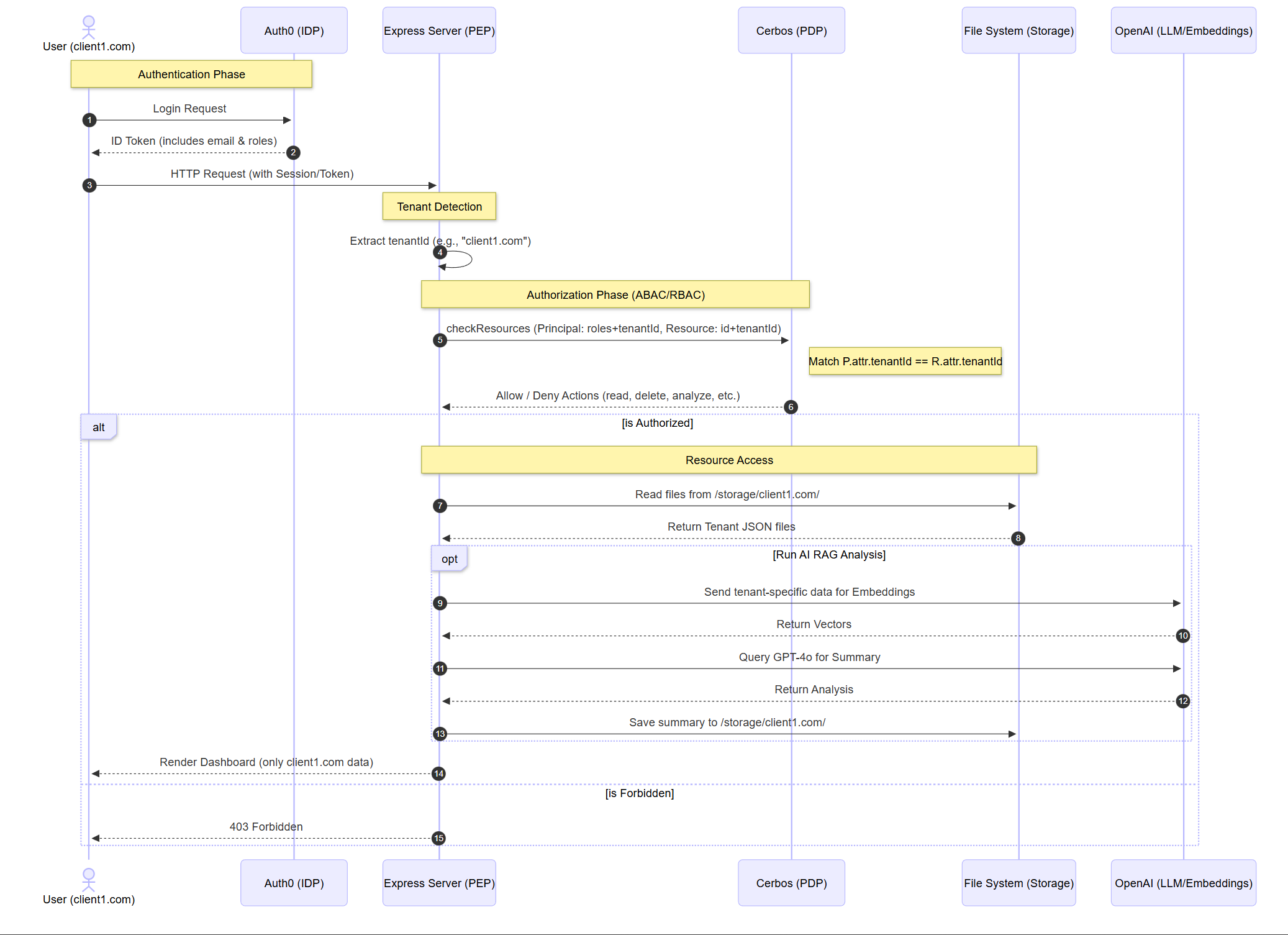
The system utilizes Auth0 for authentication, but its role extends into the authorization layer. Upon login, a Post-Login Action injects custom claims into the JWT. These claims include the user’s roles and tenantId. When a request hits the Express server (acting as the PEP), the server extracts this identity context to build the authorization request.
The Cerbos PDP in Action
Instead of checking tenant IDs within the route handlers, the PEP calls the Cerbos PDP. The policy repository contains Derived Roles, which dynamically calculate permissions based on the environment.
- RBAC: The policy checks if the user possesses the
adminormemberrole. - ABAC: The policy adds a layer of logic, such as checking business hours or sensitive tags.
- Isolation: The PDP ensures the user and the file belong to the same tenant before granting any actions.
Securing the RAG Pipeline
The project includes a multi-model workflow where a summary is generated from multiple JSON files. First, the PEP asks the PDP for permission to execute the analyze action. Because this check is externalized, the administrator can revoke analysis permissions for a specific tenant in the Cerbos policy file. This change takes effect instantly across the entire platform without a single line of code change or a server restart.
4. Conclusion: The Future of Authorization is Decoupled
In the era of Cloud-Native SaaS and AI, embedding authorization logic inside microservices is a technical debt that no organization can afford. The PEP+PDP pattern offers a clean, scalable, and audit-proof alternative. By treating policy as a standalone tier of the infrastructure, we achieve three critical goals:
- Strict Security: We guarantee tenant isolation through standardized ABAC rules.
- Cost Control: We provide granular protection and rate-limiting for expensive LLM resources.
- Operational Agility: We gain the ability to update security logic across all services instantly.
As AI continues to weave itself into the fabric of software, the need for a unified, intelligent decision layer will only grow. Projects like the JSON RAG Manager prove that with the right architecture, complexity does not have to come at the cost of security.

