by Chris | Jan 3, 2026 | Blog
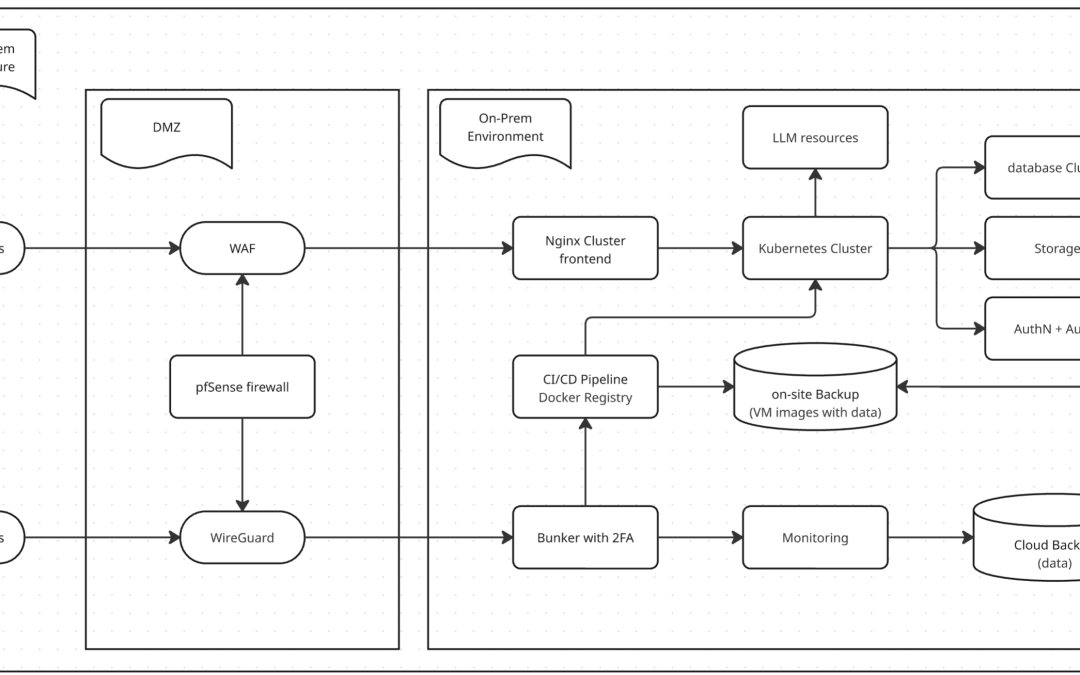
For organizations building a Modern SaaS, the architectural choice is often a painful compromise. Public cloud costs for compute are skyrocketing, yet pure on-premise environments often lack the security rigor and durability required for enterprise-grade compliance....

by Chris | Dec 31, 2025 | Blog
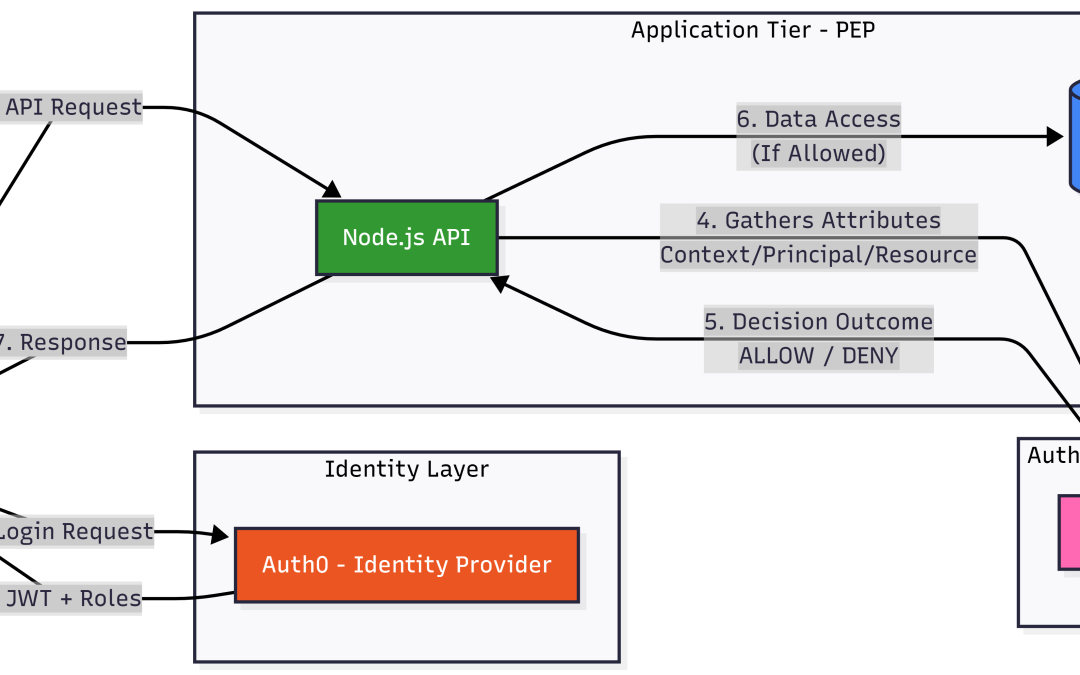
In the rapidly evolving landscape of Cloud-Native development, the intersection of Multi-Tenant SaaS and Large Language Model (LLM) integration has introduced unprecedented complexity to access control. As organizations shift from monolithic structures to distributed...
by Chris | Dec 28, 2025 | Blog
Introduction: The Invisible Crisis of Authorization Silos In the modern distributed landscape, OWASP A01: Broken Access Control has ascended to the top of the security threat hierarchy for a reason. As enterprises move from centralized monoliths to sprawling...
by Chris | Dec 17, 2025 | Blog
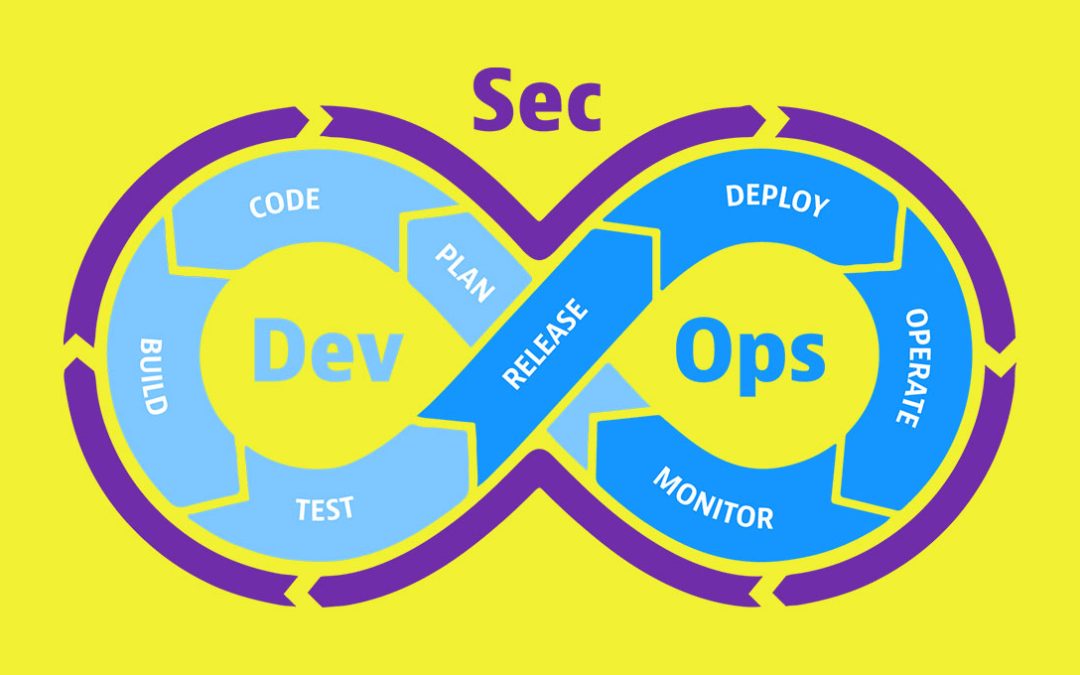
I. Introduction: The Silent Threat to the Modern Pipeline Modern cyberattacks rarely begin at the application’s external interface. Attackers now target the software supply chain—the dependencies, components, and build artifacts that development teams trust by...
by Chris | Dec 13, 2025 | Blog
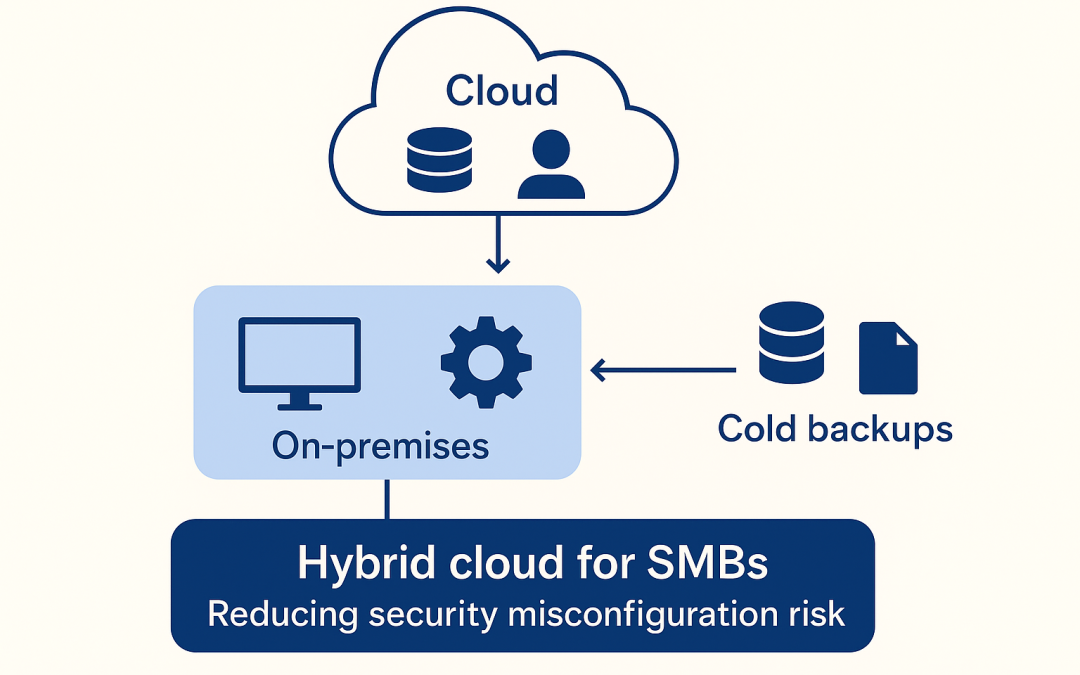
Introduction Security has become one of the defining challenges for small and medium-sized businesses. Modern IT systems are no longer simple or isolated; they are composed of cloud services, APIs, identity platforms, CI/CD pipelines, third‑party integrations, and...
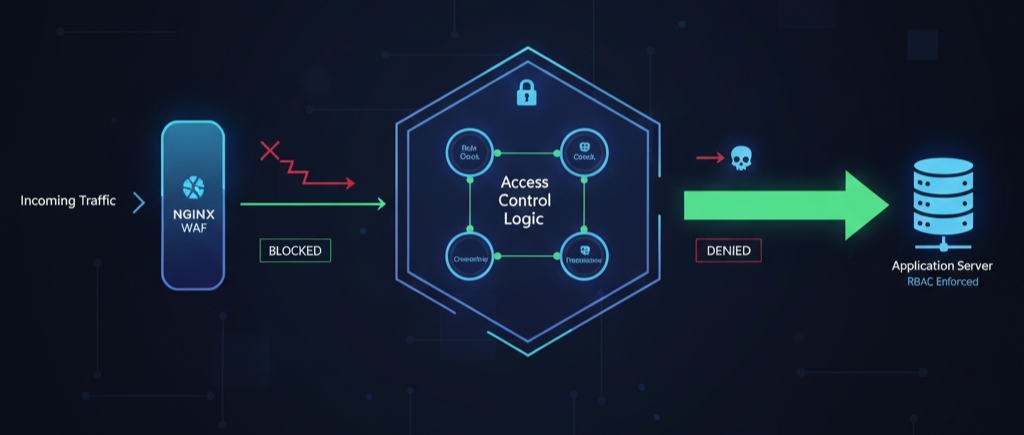
by Chris | Dec 11, 2025 | Blog
Introduction: Why A01 Remains the Top Security Risk Broken Access Control (OWASP A01) consistently ranks as the most prevalent and critical security vulnerability (refer to the official OWASP Top 10:2025 A01 Guide). This flaw occurs when users can perform actions...







