For organizations building a Modern SaaS, the architectural choice is often a painful compromise. Public cloud costs for compute are skyrocketing, yet pure on-premise environments often lack the security rigor and durability required for enterprise-grade compliance.
The reality of modern infrastructure is that compute is an expensive, replaceable commodity, whereas data is a priceless asset requiring elite protection. Most SMEs have already invested heavily in local hardware. Abandoning this for a pure-cloud model results in massive monthly “compute taxes” for resources you already own. However, the cloud offers a level of storage durability and global compliance (SOC2/GDPR) that is nearly impossible for a lean team to replicate on-site.
This article establishes a Strategic Hybrid Strategy: we keep resource-heavy, “expensive” compute on-site (utilizing replaceable local nodes), while integrating with a sophisticated storage and resilience layer that bridges local performance with cloud-scale durability.
This is the Master Blueprint. Following this overview, I will be releasing a 5-part technical deep-dive series, providing the configuration logic, scripts, and policies for each pillar.
1. Perimeter Defense: ISP Integration, DMZ & The 2FA Bunker
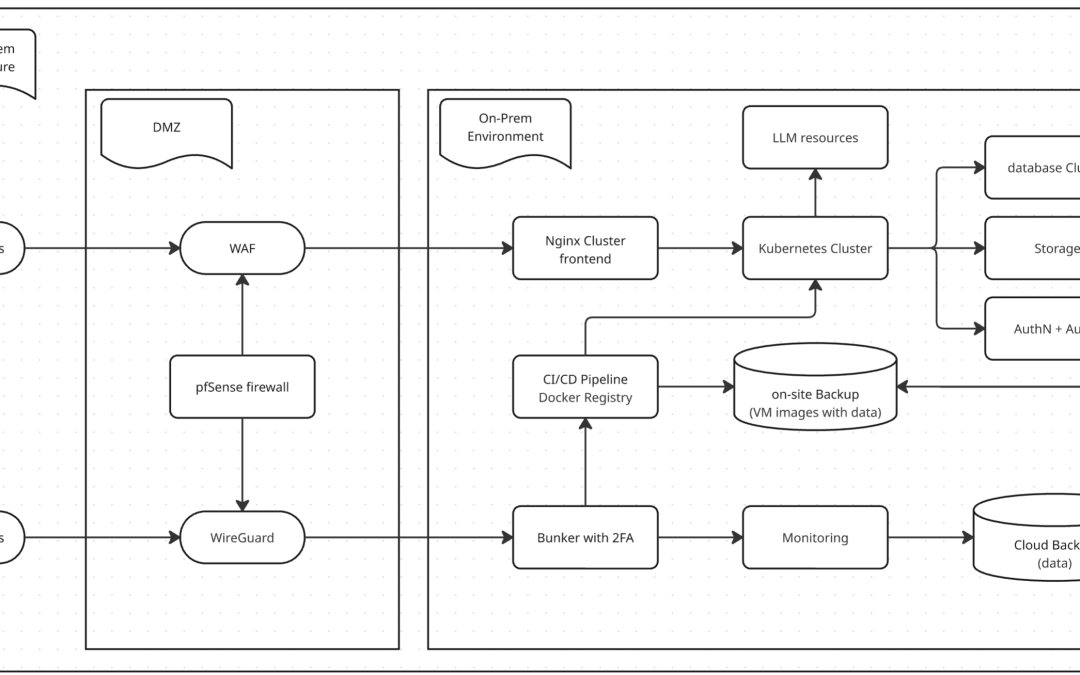
In a professional enterprise setting, a SaaS doesn’t just “sit on the web.” It is a high-security enclave within the corporate network. We start at the ISP hand-off, isolating the production data center from the general corporate office.
- The ISP & DMZ: The SaaS environment lives in a dedicated DMZ zone managed by an HA Firewall Cluster. This acts as the hardened border between the ISP’s entry point and your local server facility.
- The User Path (Nginx Cluster WAF): Public traffic is scrubbed by an Nginx Cluster WAF at the DMZ edge. This intercepts Layer 7 threats (SQLi, XSS) before they ever reach your application logic.
- The Staff Path (The 2FA Bunker): Administrative access is never public. Staff must tunnel through a VPN into the DMZ, then authenticate via a BunkerVM (Jump Box) secured with Two-Factor Authentication (2FA). No one touches production without passing through the Bunker.
Coming Next: Part 1: The Gateway – HA Firewall rules, Nginx WAF scripts, and the 2FA BunkerVM setup.
2. DevSecOps: Security-First CI/CD & Cloud-Native Immutability
We leverage GitHub Self-Hosted Runners because they provide the perfect security balance: they allow us to execute builds internally without exposing a single internal resource to the public internet. For a Modern SaaS, GitHub is safer than a self-hosted repo because it provides world-class security features an SME simply cannot maintain alone.
- Security as Code: We enforce a “No Scan, No Deploy” policy. Every build is forced through SonarQube (SQ) for code quality and Trivy for container vulnerability detection.
- Containerized Advantage: We use a Cloud-Native (K8s/Container) architecture for its security benefits: immutability and isolation. Because the compute nodes are decoupled from the data, hardware is replaceable. If a node fails, we spin up a new one without risking the core assets.
Coming Next: Part 2: DevSecOps – Secure GitHub Runners, SQ/Trivy Integration, and Containerized Security.
3. Observability & Resilience: Monitoring & Application Clusters
Uptime is a foundational pillar of modern security. In this section, we establish a robust defense through two distinct layers: intelligent visibility and application-level fault tolerance.
-
Observability (Monitoring): We utilize Zabbix for real-time visibility into physical hardware and complex business logic. Specifically, Zabbix excels at State-Based Tracking and Custom Scripting. Furthermore, we integrate Prometheus for high-velocity container metrics, while remaining mindful of its “Exporter Tax” and short-term retention limits.
-
Application Resilience: Beyond monitoring, we deploy high-availability Application Clusters. By utilizing load balancers and synchronized service nodes, the system can automatically bypass failed instances. Consequently, this ensures that the business remains operational even during partial service outages.
Coming Next: Part 3
Observability – Monitoring System
Resilience – High-Availability Clusters
4. Data Storage & Triple-Layer DR: The Storage Hierarchy
Storage in a modern SaaS environment is not merely a disk; rather, it is a tiered system designed for speed, scale, and absolute compliance. This is where we implement our final line of defense for data survival.
- The Storage Stack: We transition from simple NAS to high-performance Distributed Storage Clusters. These clusters provide the high-availability performance required for modern workloads. Furthermore, every layer enforces strict partitioning by TenantID to ensure absolute data isolation.
- Triple-Layer DR (The Hybrid Vault):
- Local Snapshots: For instant recovery from local configuration errors.
-
Cloud Fault-Tolerance: Persistent tenant data is synchronized to Cloud Object Storage (S3), leveraging cloud-scale durability for site-level failover.
-
Local Cold Archive: An offline, physical backup on-site acts as the final defense against ransomware and total cloud outages.
Coming Next: Part 4: Data Sovereignty – From Distributed Storage to Cloud S3 Sync and Cold Archive.
5. PEP/PDP: The Language-Agnostic Security Brain
Security logic must be decoupled from application code to remain auditable. In this architecture, the application is “permission-blind.”
- The PDP (Cerbos): A self-hosted brain (Policy Decision Point) managing all RBAC and ABAC policies via external YAML files.
- The PEP (Enforcer): The application layer acts strictly as a Policy Enforcement Point. Whether using Node.js, Go, or Python, the app simply asks the PDP for a “Yes” or “No” before executing any action.
Coming Next: Part 5: Modern Authorization – Decoupling Permissions with Cerbos PEP/PDP.
Conclusion
This architecture represents a rational, high-performance blueprint for Modern SaaS. It utilizes the cloud where it is strongest (Compliance & Durability) and local hardware where it is most cost-effective (Compute). It is designed to be managed by a lean team while providing a security posture that rivals global giants.