1. The Modern SaaS Dilemma: The Gap Between Scale and Skill
In the current landscape, mid-sized SaaS providers face a systemic paradox. To remain competitive, they adopt modern, distributed architectures—containers, microservices, and hybrid clouds. However, the human capital required to secure and maintain these systems is increasingly scarce.
Most SMEs operate with a lean DevOps team where “Security” is often an additional hat worn by a developer rather than a dedicated role. This leads to Configuration Drift and Silent Compromises. Traditional environments require manual intervention for breaches or misconfigurations. Engineers must receive alerts, investigate causes, and manually patch servers. For a small team, this latency is not just a downtime risk; it is a business existential threat.
2. The Paradigm Shift: An Autonomous Remediation Framework
To address the systemic risks of configuration drift and the human latency in security response, I propose a Closed-Loop Self-Healing Architecture. This framework moves beyond the traditional “Alert-and-Wait” model. We avoid relying on overstretched DevOps teams for manual triage. Instead, our system treats infrastructure as a dynamic, self-correcting organism. The goal is to enforce Immutable Infrastructure in real-time: Instead of ‘repairing’ unauthorized changes, the system obliterates and replaces them via automated IaC.
The integrity of this solution relies on a precise, four-stage telemetry-to-action pipeline, as illustrated in the following logic flow:
The Four-Stage Remediation Pipeline
- The Audit Trigger: Cerbos intercepts every transaction on the Worker Node. This provides a granular, policy-based audit trail that distinguishes between legitimate operations and “Tainted” activities (e.g., unauthorized binary execution).
- Intelligence Ingestion: Zabbix continuously consumes these Cerbos audit logs. Through custom triggers, Zabbix identifies high-risk security events that go beyond simple performance metrics.
- The Logic Bridge: Upon detecting a compromise, Zabbix executes a remote action via a WebhookAPI hosted on a dedicated API VM (the Controller). This API acts as the gatekeeper, verifying the incident and preparing the remediation payload.
- IaC Execution: The Controller invokes Terraform to execute a targeted
replaceoperation. It communicates with the Proxmox VE API to destroy the specific compromised VM and provision a fresh instance from a verified “Gold Image,” which then automatically re-mounts the secure cloud storage.
This architecture effectively mitigates the risks identified in the first section by removing the “Human-in-the-Middle” requirement.
Strategic Impact on Operations
- Eliminating Configuration Drift: Since the remediation is handled by Terraform, the new node is guaranteed to match the version-controlled state, wiping out any manual “hot-fixes” or malicious changes.
- Zero-Trust Enforcement: By using Cerbos as the primary trigger, we ensure that the self-healing logic is driven by Security Policy rather than just system uptime.
- Sustained Availability: Because the compute layer is stateless and the process is programmatic, the “Mean Time To Recovery” (MTTR) drops from hours of manual investigation to seconds of automated execution, allowing the business to maintain HA even during an active compromise.
In essence, this framework transforms IaC from a deployment tool into a Runtime Security Engine. By linking the “Eyes” of the system (Zabbix/Cerbos) directly to the “Hands” of the system (Terraform/PVE), we create an autonomous loop that maintains system integrity without requiring 24/7 manual oversight.
3. Case Study: jsonRAG — Implementing the Self-Healing SaaS
To move from theory to practice, I developed jsonRAG, a multi-tenant JSON management service integrated with LLMs. The Resilience module in this project serves as a reference implementation for an autonomous environment on Proxmox VE.
I built the jsonRAG architecture on a ‘Management-to-Workload’ hierarchy. It starts with a Controller VM (API VM), which is the only node that directly communicates with the Proxmox VE API.
Within this Controller, the infrastructure is defined and maintained through Terraform:
- The High Availability Ingress: A cluster of two Nginx nodes utilizing Keepalived for Virtual IP (VIP) redundancy.
- The Computing Layer: Two Worker Nodes responsible for the jsonRAG application logic.
- The Control Interface: The Controller VM hosts the
webhookAPI. This service acts as an execution bridge, allowing external monitoring systems to trigger internal Terraform lifecycles. By hosting the IaC state and the execution API on the same management node, we ensure that infrastructure changes are always performed from a trusted, centralized source.
Driving Resilience via Audit Trails
The resilience of jsonRAG is driven by the auditability of the Cerbos authorization engine.
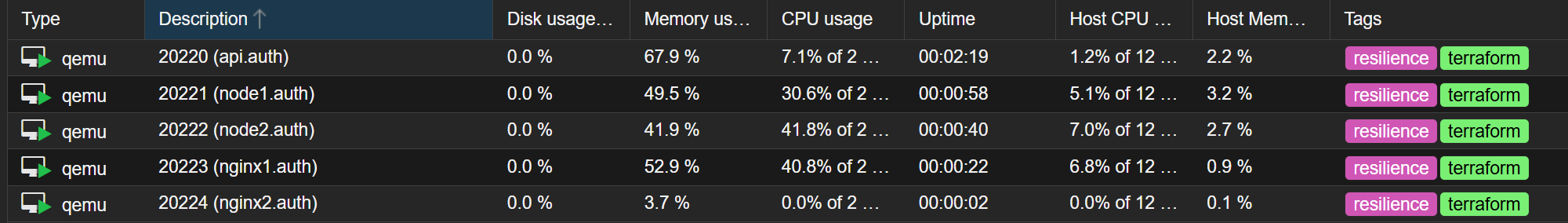
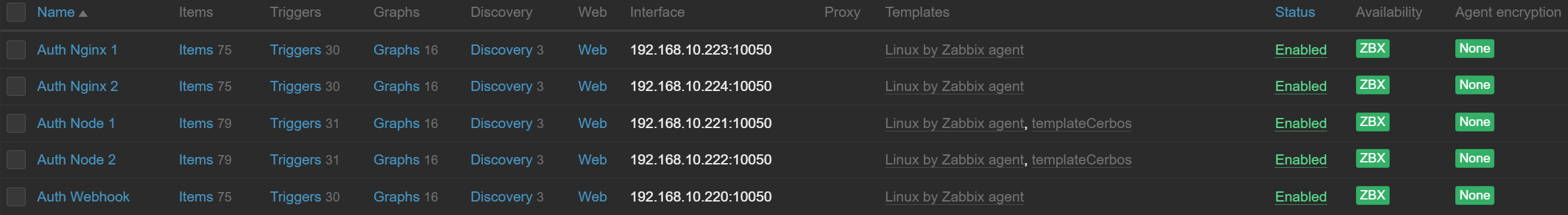
- Telemetry & Detection: As seen in the Resilience directory, Zabbix ingests Cerbos audit records to identify high-risk events. It identifies high-risk security events (e.g., unauthorized tenant data access) that go beyond simple system health.
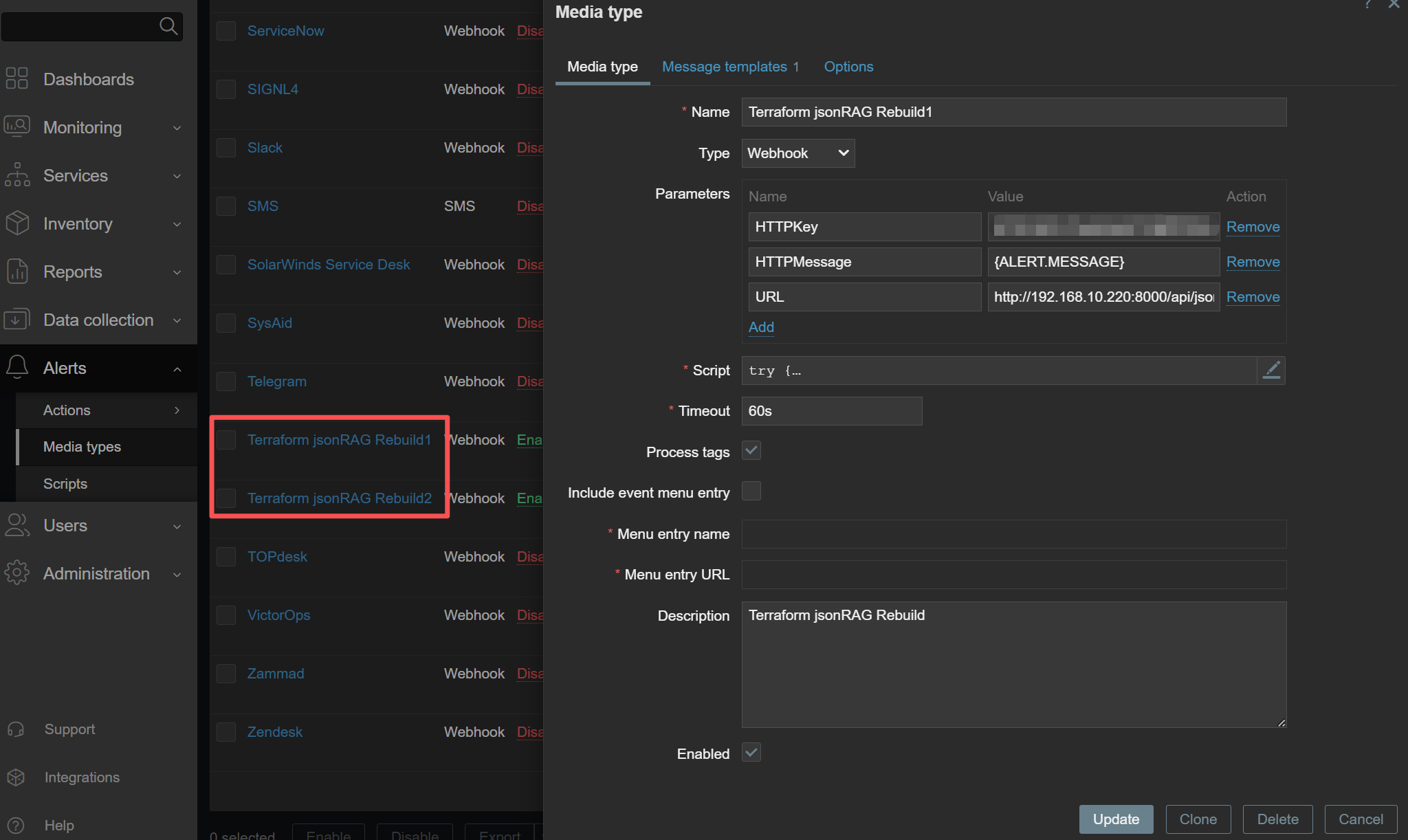
- Webhook Trigger: Upon a violation, Zabbix sends an authenticated request to the
webhookAPI.
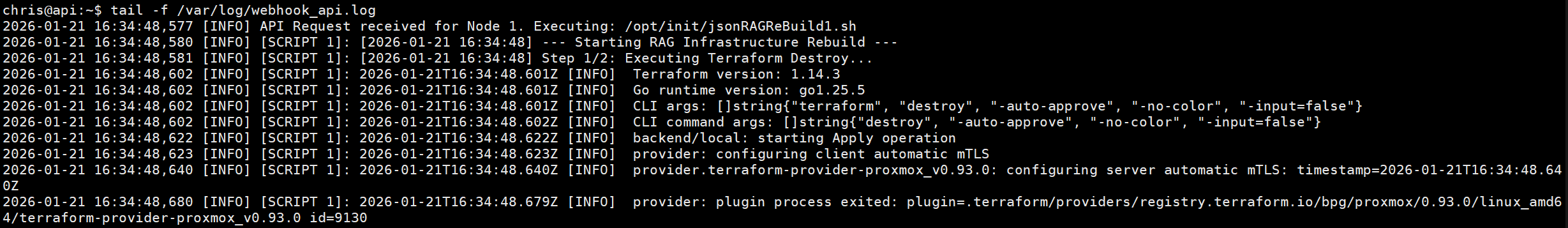
- IaC Re-provisioning: The webhookAPI parses the incoming alert. It doesn’t just “fix” a service; it utilizes the Terraform environment on the Controller to initiate a resource reconstruction. This ensures that any “tainted” VM is destroyed and a clean, verified instance is provisioned on Proxmox, maintaining the integrity of the computing cluster.
This specific implementation provides three critical benefits for resource-constrained SaaS operations:
Practical Advantages for Lean Teams
- Storage Outsourcing (Out-Sourcing as Security): As argued in my previous research on Hybrid Cloud Security, we offload persistence to Cloud Object Storage. Because the Worker Nodes are stateless, the reconstruction process does not risk data loss. The fresh VM simply re-mounts the secure remote bucket upon boot, combining the performance of local Proxmox compute with the durability of professional cloud storage.
- Reduced Human Intervention: The system functions as an automated SRE. It manages the complexities of Nginx load balancing and Keepalived failover while handling security remediation. This allows a lean team to maintain a 24/7 security posture without a dedicated SOC.
- Deterministic Recovery (MTTR): Instead of hours spent on forensic investigation and manual patching, the recovery time is reduced to the duration of a Terraform run. The system provides a predictable, clean-slate recovery that guarantees the removal of any persistent threats within the VM.
4. Conclusion: Resilience as an Engineering Discipline
Modern DevOps is shifting from “Uptime Management” to “Recovery Orchestration.” By linking the “Eyes” of the system (Zabbix + Cerbos) to the “Hands” of the system (Terraform + Proxmox), we create an infrastructure that behaves like a living organism—capable of detecting injury and regenerating its own cells.
For small teams, this is the ultimate force multiplier. The right logic and Immutable Infrastructure enable high-level resilience. This setup achieves security that traditionally required a massive operational budget. In the world of SaaS, the most secure system isn’t the one that never fails; it’s the one that knows how to be reborn.

