In Part 1, we established the “Frontline” of our SaaS—a hardened perimeter consisting of DMZ isolation and Layer 7 WAF scrubbing. However, a secure boundary is only half the battle. In a Modern SaaS environment, the greatest risk often lies in how we build and deploy software, not just how we defend the production environment.
Traditional CI/CD pipelines often create a dangerous trade-off. To achieve automation, teams frequently open internal network ports to cloud-based CI providers. Others store sensitive deployment keys in third-party environments. Consequently, for a mid-sized SaaS provider, this “convenience” introduces an unacceptable attack surface.
Part 2 of this series focuses on DevSecOps. We move deeper into the infrastructure to explore how to build a “No-Trust” deployment pipeline. By leveraging a GitHub Self-Hosted architecture combined with Cloud-Native Immutability, we ensure that security is a fundamental characteristic of every container we deploy. Specifically, we keep our internal production resources completely invisible to the public internet.
The Core Foundation: GitHub Self-Hosted Architecture
The operational prerequisite for this entire DevSecOps framework is the GitHub Self-Hosted Runner strategy. For a Modern SaaS, choosing the right CI/CD execution environment is a critical security decision. We must balance managed intelligence with local isolation.
1. The Security Balance: Why Managed GitHub Beats Self-Hosted GitLab
A common misconception among SMBs is that a self-hosted GitLab instance is more secure because of “total control.” In reality, maintaining a secure GitLab instance requires a dedicated security team for patching and hardening. Most SMEs lack this luxury. Moreover, even Red Hat recently suffered a security incident on their self-managed GitLab instance.
Therefore, we choose GitHub Enterprise because it provides world-class security features like automated patching and secret scanning. By using Self-Hosted Runners within our internal network, we gain the best of both worlds: GitHub’s top-tier platform security and our own localized, private execution environment.
Securing the Automated Execution Hub
2. The Deployment VM
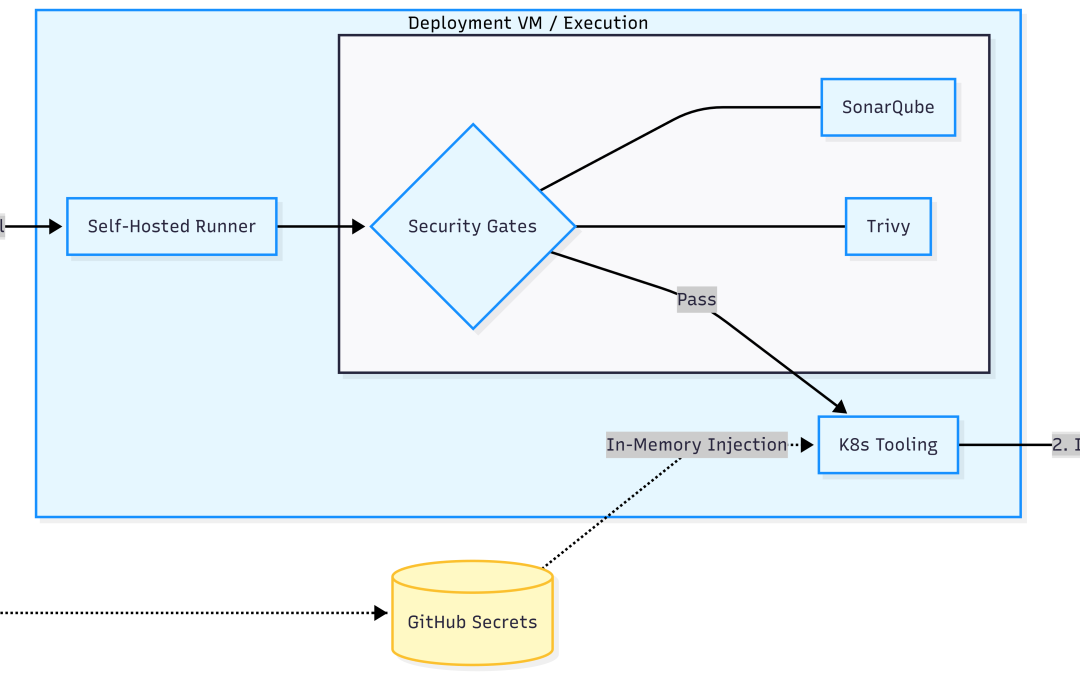
Our architecture introduces a dedicated Deployment VM located inside our internal secure zone. This VM acts as a unidirectional gateway for automation. Developers never need to log into this machine.
 Furthermore, it does not host any user-accessible services.
Furthermore, it does not host any user-accessible services.
- Zero Inbound Ports: The runner initiates an outbound-only connection to GitHub to pull jobs. Because it “calls out” to the cloud, we do not need to open any port on our firewall to the public internet. As a result, our internal production environment remains a “black box” to external scanners.
- The Internal Tooling Arsenal: This VM is an automated workshop. We pre-configure it with Docker for builds, SonarQube/Trivy for scanning, and kubectl/Helm for orchestration. These tools interact with our K8s cluster over the internal high-speed network.
3. Strategic Isolation & Secret Security
By running the CI/CD logic on our own hardware, we ensure that the “last mile” of deployment happens locally. In addition, we leverage GitHub Actions Secrets and Variables to maximize security.
- Eliminating .env Risks: We never write sensitive production data to static
.envfiles on the server disk. Instead, the Runner pulls secrets from GitHub’s encrypted vault directly into its memory at runtime. - Dynamic Manifest Generation: We use these secrets as parameters to generate deployment YAMLs on the fly. Once the deployment to the Kubernetes cluster is complete, the Runner flushes the sensitive data from memory. Consequently, even if an attacker gains access to the Deployment VM, they will find no static configuration files containing production credentials.
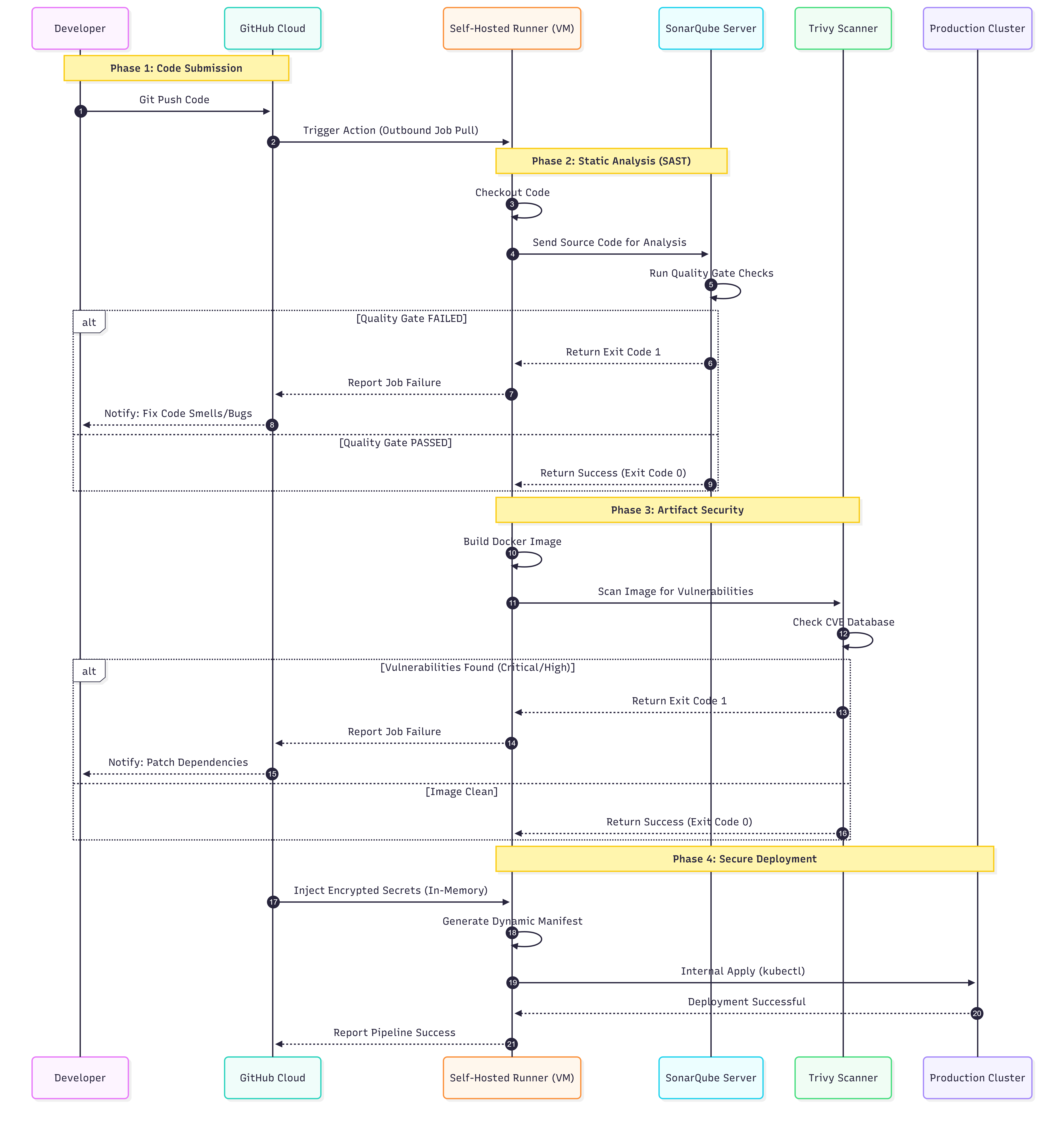
1. Security as Code: The “No Scan, No Deploy” Mandate
In our architecture, security is a non-negotiable condition of the build’s existence. We integrate automated gatekeepers directly into the Deployment VM. This allows us to shift security to the “Left,” ensuring that only verified artifacts ever reach our production cluster.
The Programmable Circuit Breaker
As explored in my analysis of OWASP A03, the most dangerous vulnerabilities slip through the cracks of a trusted pipeline. We mitigate this by treating our CI/CD pipeline as a series of Circuit Breakers:
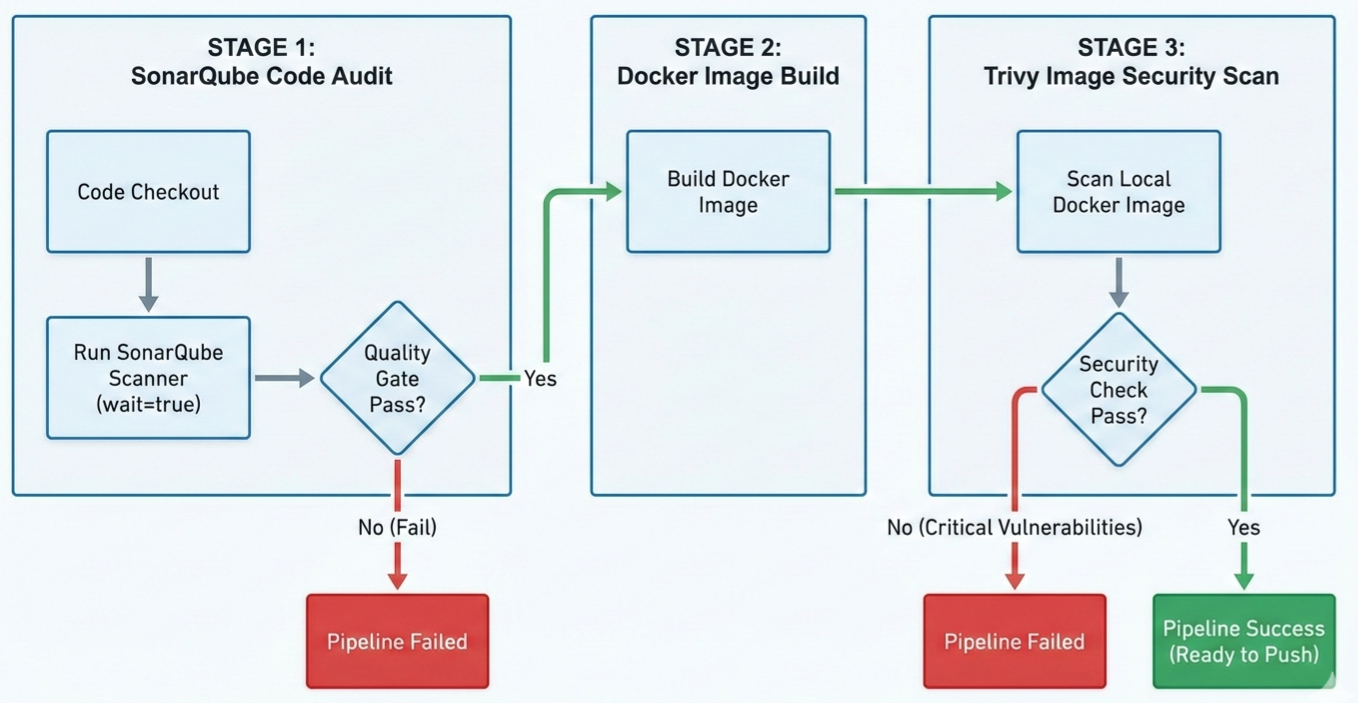
- Static Analysis Gate (SonarQube): This is the first hurdle. Before we containerize the code, it must pass a Quality Gate. This ensures we catch “Code Smells” and security hotspots. If the Quality Gate fails, the circuit breaks and the process stops.
- Artifact Integrity Gate (Trivy): Even secure code can be undermined by a compromised base image. Once the Docker build is completed locally on the Deployment VM, we use Trivy to inspect the container’s filesystem. Subsequently, this scan detects CVEs in OS packages before we tag the image for production.
Enforcing the Pipeline Gate
Unlike cloud-native CI providers that require you to push images to a registry for scanning, our strategy scans the image the moment it is built.
- Reduced Data Exposure: Sensitive build artifacts and unverified images never leave our internal network. Instead, we scan them in a “sandbox” (the Deployment VM) before promotion.
- Immediate Feedback Loop: Scanning tools share the same high-speed internal backbone as our code and container storage. Consequently, the “Scan-to-Decision” time is near-instantaneous.
- Governance by Exit Codes: As demonstrated in my CICD_Verification repository, we enforce this through exit-code governance. The architecture makes the “Deployment” phase physically impossible to reach unless the “Security” phase returns a success signal.
2. The Containerized Advantage: Immutability & Strategic Isolation
In our architecture, Kubernetes serves as a Security Isolation Layer. By decoupling compute nodes from underlying data, we transform our infrastructure into a collection of replaceable assets. In short, if a node fails, we simply terminate it and spin up a fresh, immutable instance.
Strategic Benefits of Cloud-Native Models
This transition to a Cloud-Native model provides three essential strategic benefits:
- Dynamic Resource Governance: We can prioritize resources for customer-facing services during high-traffic periods. Specifically, strict
resource quotasensure that a spike in one microservice cannot starve the rest of the system. - Polyglot Development & Secure Outsourcing: Containers allow us to use the best tool for the job. We can write different modules in different programming languages, such as Java, Python, Node.js, or PHP. Furthermore, this enables Controlled Outsourcing. External teams can develop specific components without ever gaining access to our host’s core data assets.
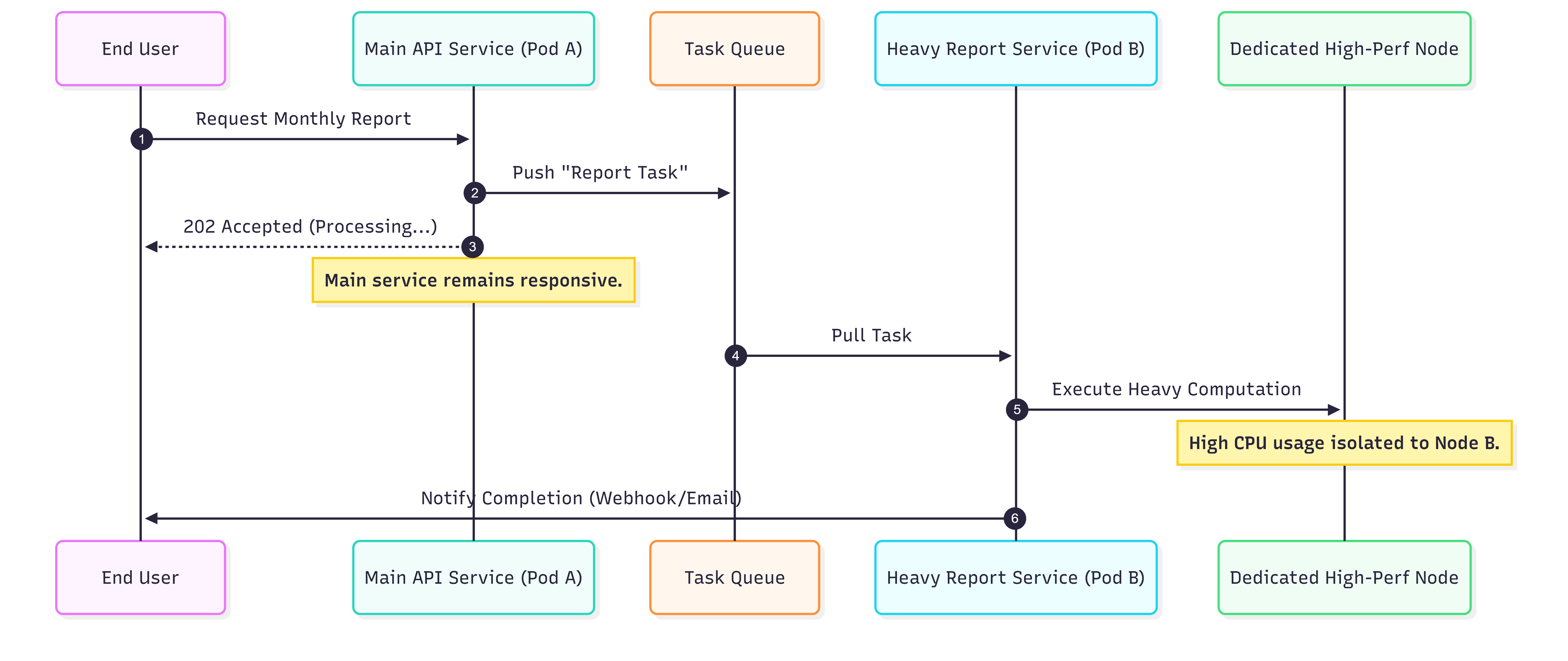
- Functional Decoupling of “Heavy” Tasks: We isolate resource-intensive operations from the primary API. For example, generating massive monthly financial reports happens on dedicated pods. By scheduling these “Heavy-Compute” pods on isolated nodes, we ensure background workloads never degrade the user experience.
*Note: Cloud-Native architecture is a vast subject. We will dedicate a standalone article in the future to explore the specific configurations of Kubernetes namespaces, pod security policies, and service meshes that make this possible.
Conclusion: Securing the “Last Mile” of Delivery
By shifting from public CI/CD runners to an internal Self-Hosted architecture, we have effectively eliminated the traditional trade-off between convenience and security. Our Deployment VM now acts as a silent sentinel. Specifically, it ensures that every line of code undergoes scrutiny by SonarQube and every container is hardened by Trivy before it ever touches our production environment.
In addition, the beauty of this Cloud-Native approach lies in its inherent resilience. Since our environment is immutable and our deployments are fully automated, we no longer fear hardware failure or local configuration drift. Consequently, we have successfully decoupled our “Security Intelligence” (managed by GitHub) from our “Security Execution” (managed by us). This strategy keeps our internal network a total “black box” to the outside world.
In the upcoming Part 3, we will move from the pipeline to the “Heart” of the SaaS: Data Sovereignty and Hybrid Connectivity. We will explore how to manage persistent data across this architecture and how to securely bridge the gap between local resources and the public cloud without losing control of your most valuable assets.