Introduction: The Invisible Crisis of Authorization Silos
In the modern distributed landscape, OWASP A01: Broken Access Control has ascended to the top of the security threat hierarchy for a reason. As enterprises move from centralized monoliths to sprawling microservice meshes, the traditional “Gatekeeper” model has fractured. Today, a single user request might traverse five different services, each attempting to verify permissions using fragmented, inconsistent, and often hard-coded logic. This is the “Authorization Silo” crisis: a state where security policies are hidden in source code, making them impossible to audit, difficult to update, and prone to catastrophic overlaps.
For many organizations, the struggle lies in the inability to maintain a Unified Security Posture. When a developer hard-codes a check like if (user.role == 'admin'), they are creating a permanent security debt. What happens when “Admin” needs to be restricted from sensitive financial data during off-hours? The developer must refactor, retest, and redeploy. In a fast-paced CI/CD environment, this friction leads to “Access Control Rot,” where permissions are either too permissive—leading to data leaks—or too restrictive, stifling business agility.
The risk is not merely theoretical. Broken access control leads to Horizontal Privilege Escalation (accessing other users’ data) and Vertical Privilege Escalation (gaining unauthorized administrative rights). To survive the compliance and security demands of 2025, enterprises must stop treating authorization as a secondary feature of their code and start treating it as a primary tier of their infrastructure.
The Solution: Decoupling Authorization with PEP & PDP
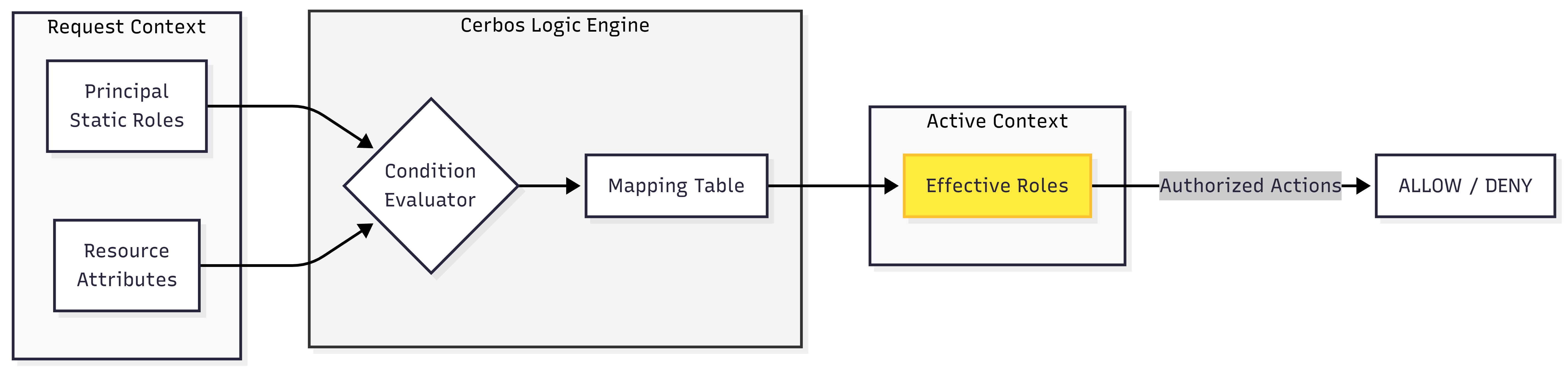
To neutralize A01, we must adopt a Decoupled Authorization framework. This architecture relies on two critical components: the Policy Enforcement Point (PEP) and the Policy Decision Point (PDP).
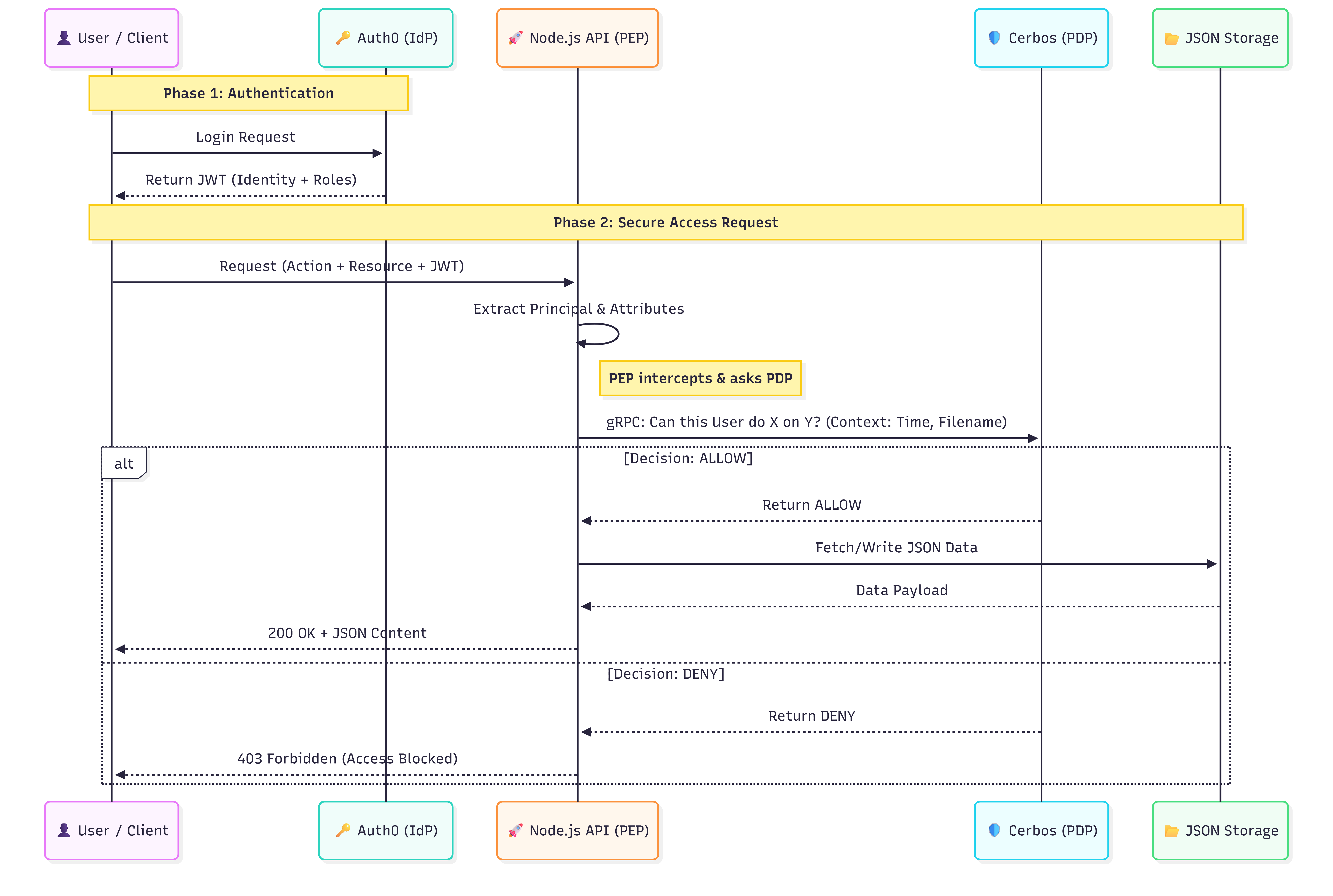
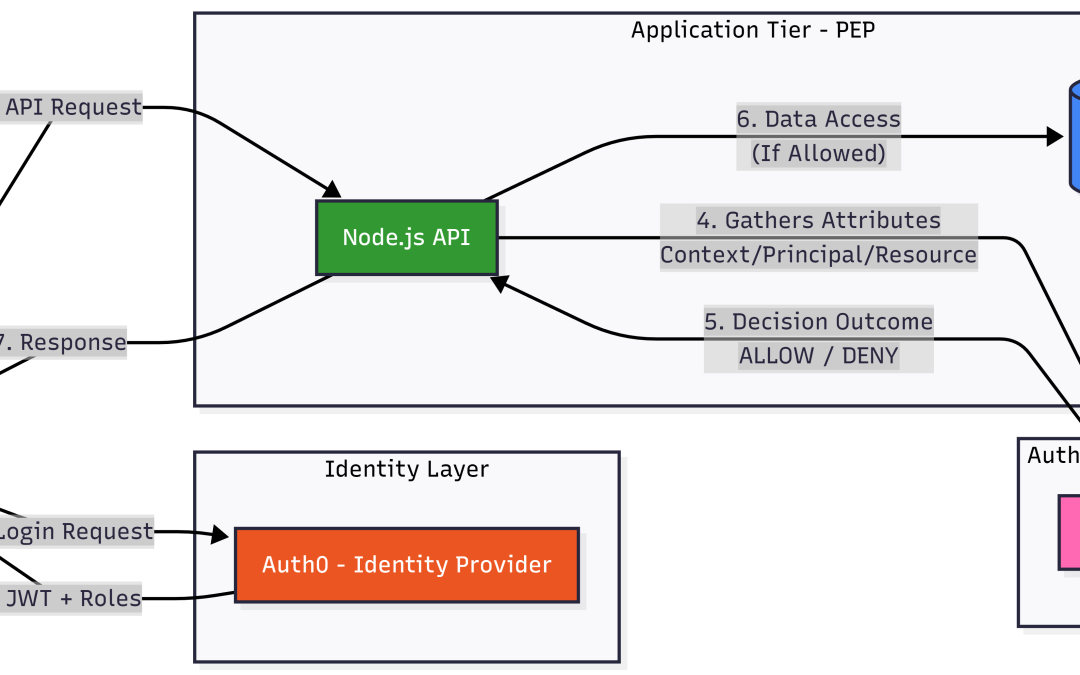
- The PEP (The Application): The PEP’s only job is to stop the request and ask, “Is this allowed?” It doesn’t know why a request is allowed; it simply enforces the answer.
- The PDP (The Brain): The PDP, powered by an engine like Cerbos, holds the centralized logic. It takes the “Who” (Principal), the “What” (Resource), and the “Context” (Environment), evaluates them against YAML-defined policies, and returns a binary
ALLOWorDENY.
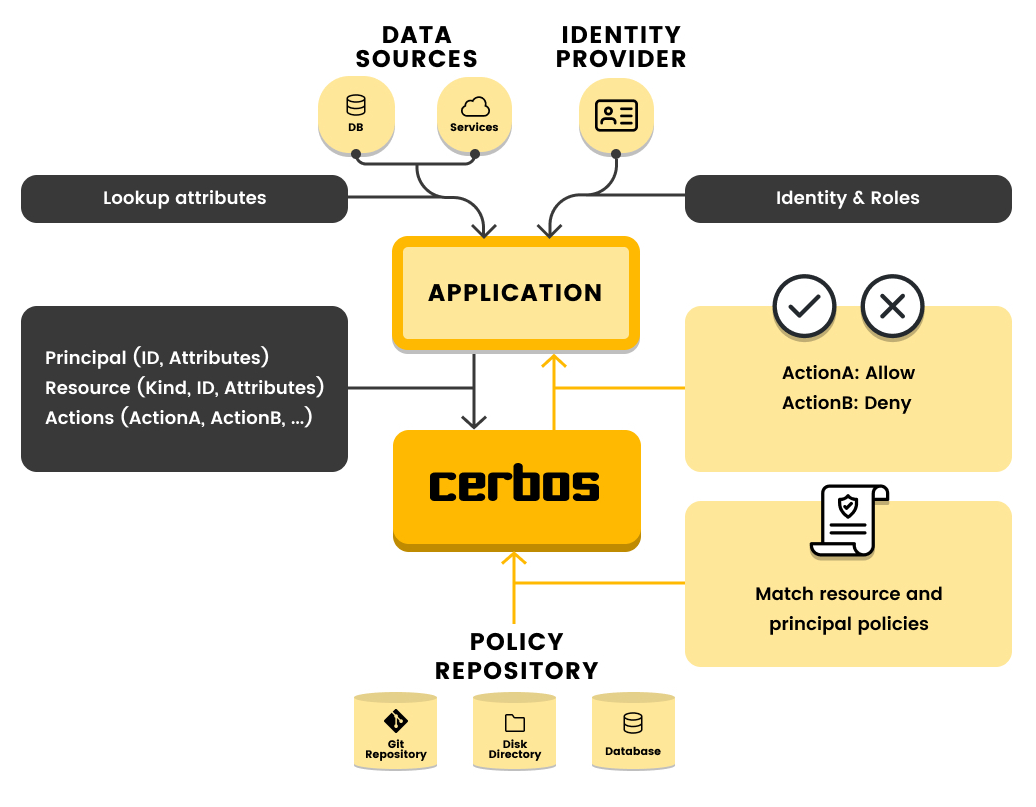
This separation allows security teams to modify policies in the PDP without touching the application’s source code. By integrating Auth0 as the Identity Provider, the application receives a cryptographically signed JWT. The PEP then passes this identity to the PDP, creating a seamless, audit-ready flow that eliminates hard-coded logic and centralizes governance.
Deep Dive: Evolution from RBAC to ABAC
To understand why this solution is effective, we must distinguish between two fundamental access control philosophies:
1. RBAC (Role-Based Access Control)
RBAC is the “Identity-Only” approach. It assigns permissions to roles (e.g., Manager, Editor, Guest). While simple, RBAC is “context-blind.” It cannot distinguish between a Manager accessing a file at 2:00 PM on a workday versus 2:00 AM on a Sunday from a restricted IP range. This lack of granularity is a primary driver of Broken Access Control.
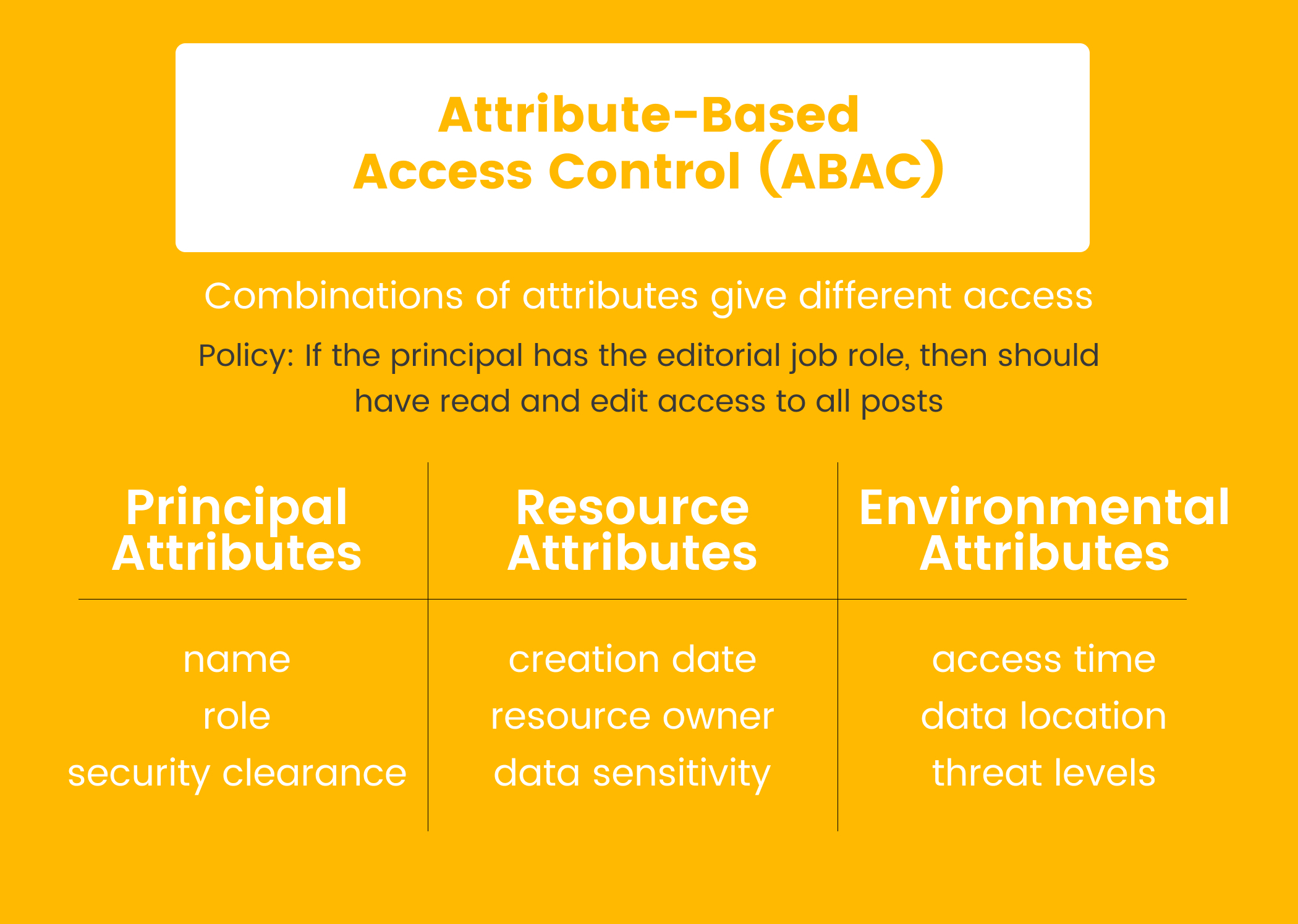
2. ABAC (Attribute-Based Access Control)
ABAC is the “Context-Aware” approach. It evaluates permissions based on Attributes:
- Subject Attributes: User’s role, department, or security clearance.
- Resource Attributes: File sensitivity, ownership, or tags (e.g.,
release,internal). - Environmental Attributes: Current time, geographic location, or device health.
Derived Roles serve as the bridge between these two. They allow us to take a standard RBAC role (Member) and “derive” a new state based on resource attributes. In our sample JSON Management System, a user is only a “Member” if the resource they are touching is not marked as sensitive. If the attribute changes, the role effectively vanishes.
Detail: Engineering a Resilient Defense
Using the sample jsonManagerment_Cerbos repository as a reference, let’s explore how these concepts manifest in a real-world defensive strategy.
1. The “Sensitive” Guardrail (BOLA Prevention)
Broken Object Level Authorization (BOLA) occurs when an attacker manipulates a resource ID to access data they shouldn’t. We mitigate this in the PDP/policies/json_file_derived_roles.yaml by ensuring that high-privilege roles are contextually revoked for sensitive files:
# Derived Role Logic: Preventing Admin Overreach
- name: admin
parentRoles: ["admin"]
condition:
match:
expr: "!R.id.matches('(?i)sensitive')"
This ensures that even if an Admin account is compromised, the “Sensitive” data remains isolated. The policy engine performs a regex check on the resource ID (R.id) before granting the effective role.
2. Temporal Compliance (Environment Attributes)
Enterprise security often requires “Just-in-Time” or “Within-Hours” access. Hard-coding this in Node.js is a nightmare. In our Cerbos policy, we implement this as an environmental attribute check:
# Resource Policy: Work-Hours Constraint
- actions: ["create"]
effect: EFFECT_ALLOW
derivedRoles: ["member"]
condition:
match:
expr: "request.action == 'create' ? (now.getDayOfWeek() >= 1 && now.getDayOfWeek() <= 5) : true"
This protects the system from automated weekend attacks using valid credentials—a common vector for data tampering.
3. The Release Filter (Dynamic Resource Discovery)
For the User role, we implement a positive-filter ABAC rule. The user can only “see” what is explicitly tagged for them. If the file name doesn’t contain release, the user derived role is never activated, and the PEP returns a 403 Forbidden.
Business Value: Why This Matters to the Enterprise
Implementing this decoupled ABAC architecture isn’t just a technical exercise; it’s a strategic business move:
- Accelerated Compliance: Whether it’s SOC2, GDPR, or HIPAA, auditors require proof of who accessed what and why. Centralized PDP logs provide an instant audit trail of every decision.
- Developer Productivity: Developers stop writing security logic and start writing business features. Security becomes “Configuration,” not “Code.”
- Zero Trust Readiness: This architecture is the foundation of Zero Trust. It moves the decision point as close to the resource as possible and evaluates every single request based on real-time context.
Conclusion
OWASP A01 is a symptom of architectural stagnation. In 2025, staying secure means moving beyond the rigid, role-only systems of the past. By leveraging Auth0 for identity and Cerbos for attribute-based policies, you can build a JSON management system—or any enterprise application—that is not only secure by design but agile by nature.
Stop hard-coding your trust. Decouple your authorization.
Technical Resources:
- GitHub Repository: Multi-Role JSON Management System
- Documentation: Cerbos ABAC Patterns
- Security Standard: OWASP Top 10:2025 A01
- OWASP A01: WAF, ModSecurity, and RBAC Layered Defense