This project is a high-performance, secure file management showcase. It demonstrates the industry-standard Decoupled Authorization architecture, separating Identity Authentication (Auth0) from Granular Access Control (Cerbos).
link: https://github.com/ChrisXHLeung/jsonManagerment_Cerbos
Solution in detail: https://www.chriscn.cn/decoupled-abac-architecture/
🏗️ System Architecture
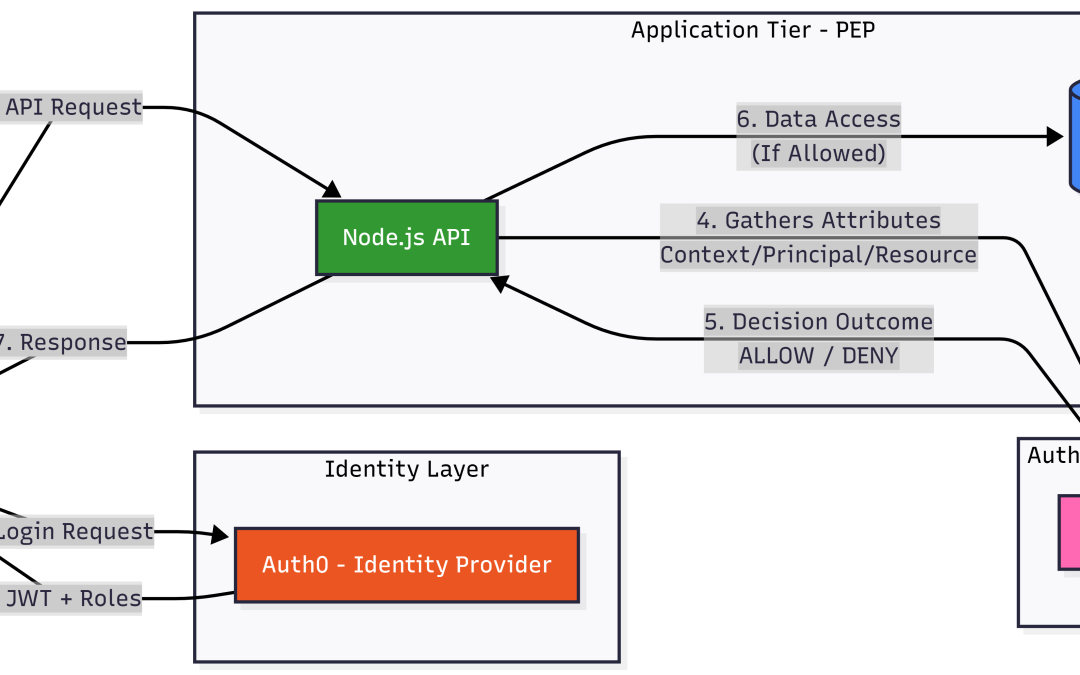
The system operates as a Policy Enforcement Point (PEP), delegating all logic to a centralized Policy Decision Point (PDP).
- Identity Layer (OIDC): Auth0 handles user sessions and issues JWTs containing role claims.
- Authorization Layer (ABAC): Cerbos evaluates requests against YAML-defined policies using real-time attributes (time, filename).
- Application Layer (PEP): A Node.js service that manages JSON I/O and enforces the decisions received from Cerbos via gRPC.
👥 Access Control Logic (ABAC)
Unlike traditional static RBAC, this system uses Attribute-Based Access Control (ABAC) to enforce dynamic rules.
🔐 Global Security Guardrails
- Sensitivity Filter: Any file matching
(?i)sensitivein its name is strictly isolated. No role (including Admin) can delete or modify these files via the standard API path. - Release Filter: The User role is restricted to a “Discovery Mode,” only seeing files tagged with
release.
📊 Permission Matrix
| Action | User (Observer) | Member (Contributor) | Admin (Superuser) |
|---|---|---|---|
| List & Read | ✅ release files only |
✅ All non-sensitive | ✅ Full Access |
| Create | ❌ Denied | ✅ Work Hours Only¹ | ✅ Full Access |
| Update | ❌ Denied | ❌ Denied | ⚠️ Non-sensitive only |
| Delete | ❌ Denied | ❌ Denied | ⚠️ Non-sensitive only |
¹ Time Attribute: Member
createactions are restricted to Mon–Fri, 09:00–17:00 UTC.
📂 Repository Structure
.
├── PDP/ # Policy Decision Point (PDP)
│ ├── conf.yaml # Cerbos server configuration
│ └── policies/ # ABAC/RBAC logic defined in YAML
└── PEP/ # Policy Enforcement Point (PEP)
├── storage/ # Flat-file JSON database
├── views/ # UI Templates (EJS)
└── index.js # Express logic & Cerbos gRPC Client
🛠️ Tech Stack Highlights
- Communication: gRPC for ultra-low latency between API and Authorization engine.
- Identity: OpenID Connect (OIDC) flow with PKCE.
- Policy Engine: Cerbos – stateless, scalable, and audit-ready.
- Express Middleware: Custom middleware to bridge JWT claims to Cerbos principal context.

I really like your writing style, good info, thanks for posting :D.