Introduction
Security has become one of the defining challenges for small and medium-sized businesses. Modern IT systems are no longer simple or isolated; they are composed of cloud services, APIs, identity platforms, CI/CD pipelines, third‑party integrations, and constantly evolving infrastructure. As complexity grows, so does the attack surface. For organizations with 10–100 employees, security expectations continue to increase, while available people, time, and budget remain fundamentally constrained.
This tension is clearly reflected in the OWASP Top 10 2025, where A02: Security Misconfiguration remains one of the most critical and persistent risks. Its prominence is not because organizations misunderstand security principles, but because they lack the operational capacity to execute and continuously maintain those principles over time. In smaller organizations, security configuration is rarely a one‑time activity—it is an ongoing operational burden that accumulates risk as systems evolve.
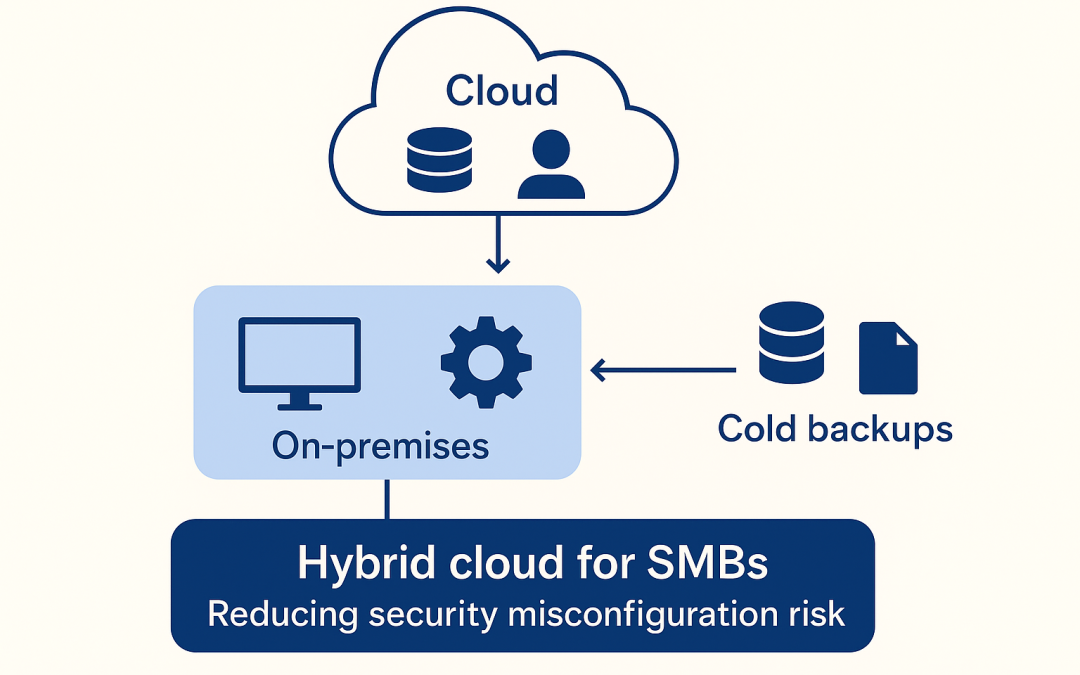
Conventional security thinking often assumes that sensitive data must be kept “in‑house,” while cloud platforms are treated as inherently riskier. At first glance, placing critical databases and customer records in the cloud while keeping compute workloads on‑premises may therefore sound counterintuitive. This article deliberately challenges that textbook intuition. Based on real‑world SMB constraints, it argues that a hybrid cloud model—where critical data is hosted by mature, compliant cloud providers, compute‑heavy workloads remain on‑premises, and offline cold backups are maintained locally—offers a more effective and cost‑efficient way to reduce OWASP A02 Security Misconfiguration risk.
Understanding OWASP A02: Security Misconfiguration
OWASP A02: Security Misconfiguration does not simply mean “someone configured something incorrectly.” In practice, it describes systems whose security depends on ongoing, precise, and expert configuration that must be maintained flawlessly over long periods of time.
Common causes include insecure defaults, overly complex configurations, configuration drift between environments, forgotten temporary changes, missing hardening, and unmonitored adjustments. What ties these together is not negligence, but operational reality. As systems grow more complex, the probability that every configuration remains correct steadily approaches zero.
For SMBs, A02 is therefore not an edge case—it is a structural risk.
The GitLab vs GitHub Reality: A Practical Example
A useful analogy for understanding A02 in practice is the difference between self‑hosted GitLab and GitHub Enterprise (cloud).
From a purely theoretical perspective, a self‑hosted GitLab instance offers maximum control. In reality, however, its security depends on:
- Continuous patching and upgrades
- Secure CI/CD runner configuration
- Access control and token lifecycle management
- Network exposure and firewall rules
- Log monitoring and incident response
- Regular security reviews and audits
Maintaining this securely requires a dedicated, experienced team and disciplined operational processes. Most SMBs simply do not have this capacity.
By contrast, GitHub Enterprise benefits from large, specialized security teams, automated patching, continuous monitoring, threat intelligence, and mature incident response processes. As a result, a cloud‑hosted GitHub Enterprise account is, in practice, far more secure than most self‑hosted GitLab deployments.
This gap is not theoretical. Even large, security‑mature organizations can struggle. On October 2, 2025, Red Hat disclosed a security incident involving its consulting GitLab instance, despite being one of the most experienced enterprise Linux and security vendors in the industry (official incident disclosure). While this example may not be perfectly analogous to all environments, it clearly illustrates a key point:
If organizations with deep expertise and resources can still experience security failures in self‑managed platforms, small and medium‑sized businesses should not assume they can consistently do better.
The lesson is not that GitLab is insecure. The lesson is that self‑managed critical systems demand a level of continuous security scrutiny that most SMBs cannot realistically sustain.
Why Cloud‑Hosted Critical Data Reduces A02 Risk
This same logic applies directly to databases and customer records. Hosting critical data on mature cloud platforms does not eliminate risk, but it significantly reduces misconfiguration risk by design.
Managed cloud database services typically enforce:
- Secure‑by‑default configurations
- Mandatory encryption at rest and in transit
- Opinionated identity and access models
- Automated patching and upgrades
- Platform‑level monitoring and auditing
- Compliance with standards such as ISO 27001 and SOC 2
From an OWASP A02 perspective, the key advantage is not that cloud providers are “more careful,” but that they remove entire classes of configuration decisions from the customer.
This is not outsourcing security; it is reducing the configuration surface area that humans can get wrong.
Why Compute‑Heavy Workloads Often Belong On‑Premises
A hybrid approach does not mean moving everything to the cloud. High‑compute workloads—such as batch processing, analytics, simulations, or training jobs—often make more sense in private or on‑premises environments.
These workloads:
- Are costly and unpredictable when billed on‑demand in the cloud
- Rarely store primary customer data
- Are often reproducible from source inputs
- Benefit from fixed‑cost, high‑utilization infrastructure
From a security standpoint, compute nodes are also more disposable. A compromised compute environment may require rebuilding systems, but it rarely represents an irreversible loss.
Compute is replaceable. Data is not.
The Role of Offline Cold Backups
Local offline cold backups provide an additional layer of resilience without significantly increasing misconfiguration risk. Because they are offline, non‑exposed, and rarely accessed, they have minimal configuration complexity.
Cold backups protect against:
- Cloud account compromise
- Ransomware
- Catastrophic provider outages
- Extreme disaster recovery scenarios
Crucially, they improve resilience without introducing new A02 attack surfaces.
Architecture Comparison Through the A02 Lens
| Architecture | A02 Risk Level | Explanation |
|---|---|---|
| Fully self‑managed | High | Configuration complexity exceeds organizational capacity |
| Fully cloud, self‑managed | Medium | IAM and network complexity remain high |
| Cloud‑managed data + on‑prem compute + cold backup | Low | Minimal configuration surface and clear responsibility boundaries |
Conclusion
This architecture may appear to contradict traditional security teaching, but it is not based on misunderstanding. It is based on operational reality.
For 10–100 person organizations, the most secure system is not the one with maximum theoretical control, but the one that is hardest to misconfigure over time. By hosting critical databases and customer records on mature cloud platforms, keeping compute‑heavy workloads on‑premises, and maintaining offline cold backups, SMBs can materially reduce OWASP A02 Security Misconfiguration risk while remaining cost‑efficient and operationally sustainable.
Further Reading
If you are interested in how similar risk-surface reduction thinking applies to OWASP A01: Broken Access Control, you may find the following article useful:
- OWASP A01: WAF, ModSecurity, and RBAC Layered Defense — An analysis of how WAFs, ModSecurity rules, and RBAC can be combined to mitigate access control failures in real-world environments.